- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- 10 Reasons to Love Passwordless #10: Never use a password
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In this series, Microsoft identity team members share their reasons for loving passwordless authentication (and why you should too!). Pamela Dingle closes the series with a post about the tighter security of passwordless authentication.
Here we are at the last of our Ten Reasons to Love Passwordless blog series! This last reason is more than closing the Ten Reasons blog series, it is about choosing to close a chapter on the past – because passwordless authentication means we can finally say goodbye to the password.
Password authentication has been around for over 60 years and has always been challenging. A password is supposed to act as a key to help the right person access an account while also operating as a security barrier to protect the account from attackers. However, 80% of hacking-related breaches involve either stolen or weak passwords that were easily guessed by the cybercriminals. Phishing, password spray, and credential stuffing attacks are all attacks that don’t involve an attacker using fancy math to get into your account – instead these attacks rely on you as a statistically predictable human. Attackers know that we humans will type our passwords without due care into a web page that looks mostly reputable. That we don’t set a different password at every website we use. That 1 out of 100 of us have easily guessed passwords like Spring2021! protecting a critical account at this very moment. That they can use 30 year old password attack tools and still succeed, because we use 30 year old protocols that are vulnerable to them. Attackers don’t have to be smart to make money from password theft, just opportunistic. Wouldn’t it be great if we could take that opportunity away?
Traditional multifactor authentication (aka MFA) presents a more secure way for users to access their accounts and resources – password plus another factor. Microsoft supports and encourages multiple ways to use MFA! Adding a second factor to your authentication reduces the probability of account compromise by 99.9%, because it ruins the instant effectiveness of password-based attacks. MFA makes user authentication much safer, but it does impact the user experience. MFA also leaves the oh-so-vulnerable password as part of the equation.
Passwordless authentication is a form of multifactor authentication that replaces the password with a secure alternative. One of the underlying principles of passwordless authentication is to eradicate the use of passwords and thereby eliminate their value for attackers. As I hope you have seen in many of our previous blog entries, passwordless authentication methods have protections against the types of attacks that represent easy money for criminals. Replacing passwords with passwordless authentication may not completely prevent all attacks, but we can make successful attacks much more expensive to perpetrate.
Passwordless methods don’t require users to enter their passwords anymore, but what if the account has a password attached to it, from initial setup? That password is less dangerous because it is not in use regularly, which is good, but there is a difference as a user between choosing not to use your password and knowing that nobody else can either. The most secure option would be for the password associated to an account to disappear forever! After all, it is tough to compromise an authentication method that doesn’t exist. You might ask, is there a way to make this happen, other than setting a long random password and forgetting it? There will be soon.
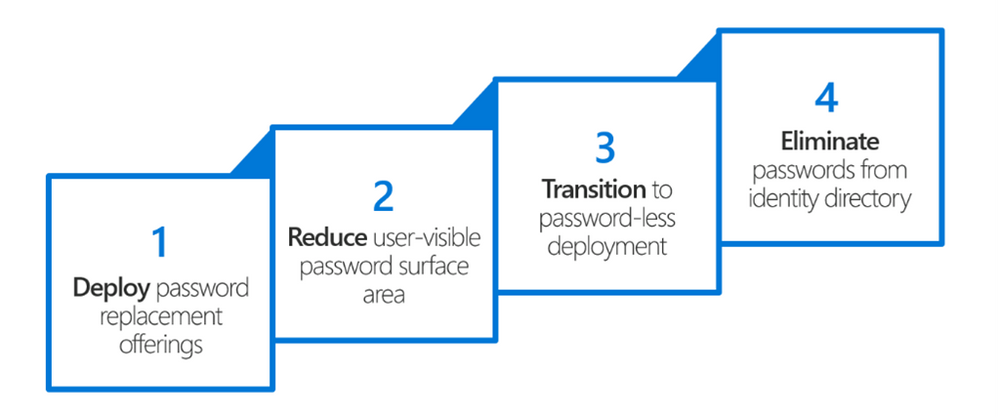
Microsoft has defined a four-step approach to end the era of passwords:
The strategy you see here seems simple, doesn’t it? But let’s just say it has been a journey. It has required singular vision, as well as collaboration both internally across many of our products and externally in our standards-based efforts. We stand today at step #3, and we are on the verge of getting to step #4. Here is a quick taste of where these steps have taken us:
-
Deploy password replacement offerings:
- Introduced by Microsoft in Windows 10, Windows Hello uses biometric sensors or a PIN to verify a user’s identity when signing into work or personal accounts from a PC.
- The Microsoft Authenticator app generates encrypted messages that allows users to verify their identity with a built-in biometric or a PIN when signing into their work or personal accounts from a mobile phone.
- Via the FIDO2 family of specifications, any website can request a phishing resistant credential from supported Microsoft, Apple, and Google platforms or from certified USB or NFC security keys.
-
Reduce user-visible password surface area:
- Login experiences across Microsoft transition to an ‘identifier-first’ flow, meaning users are no longer asked for a password at the same time they are asked for their username.
-
Transition to passwordless deployment:
- Legacy authentication support is replaced with modern authentication support, and hard-coded assumptions about the omnipresence of passwords are found and removed.
- Users sign into their accounts with one of the password replacement technologies and use single sign-on to access all their resources.
-
Eliminate passwords from identity directory (future):
- Administrators can choose whether passwords are required, allowed or simply don’t exist for a set of users, and users can choose either to not set a password when an account is created, or to remove their existing password from an account.
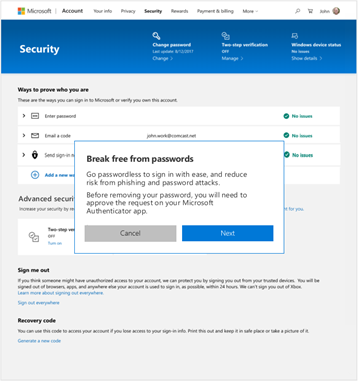
When Microsoft gets to step 4 in our vision, those of you who are security minded will have the power not only to use more secure authentication methods, but to eliminate less secure authentication methods. In Spring 2021, we will launch the functionality to allow password removal on Microsoft consumer accounts. Choosing to go passwordless means that instead of signing in with the Microsoft account password, users will verify sign in with the Microsoft Authenticator app. Additional forms of passwordless authentication such as Windows Hello and FIDO2 are also available to round out the options.
I can’t tell you how excited I am to see us get to these later stages of our Microsoft passwordless vision, but success in these four steps really just gets us to the starting line when it comes to living without passwords in our daily work, home, and school lives. As passwordless authentication in Azure AD is now generally available, we hope to see meaningful change in adoption rates for multifactor and passwordless authentication. We feel confident now that there are usable, meaningful alternatives to passwords available, and most importantly, the methods you see today are only the beginning. We now have the platform support, the vendor ecosystem, and the standards frameworks needed to foster new innovation and to improve our security posture over time.
I encourage you all to try passwordless authentication on for size, and I hope we have given you 10 really great reasons as to why this journey might be worthwhile. On behalf of all my co-authors, we hope this series has helped you understand passwordless authentication and has provided some useful tips for deploying in your organization. The more we can embrace passwordless as the norm the more we can protect ourselves and our organizations. And – to all of the current and past Microsoft employees who have waited for years to see our vision finally result in real day-to-day usage – we made it!
Check out the other posts in this series:
- Temporary Access Pass is now in preview
- What's New in Passwordless Standards, 2021 edition!
- 10 Reasons to Love Passwordless #1: FIDO Rocks
- 10 Reasons to Love Passwordless #2: NIST Compliance
- 10 Reasons to Love Passwordless #3: Why biometrics and passwordless are a dream combination
- 10 Reasons to Love Passwordless #4: Secure your digital estate, while securing your bottom line
- 10 Reasons to Love Passwordless #5: The Ease of Use and Portability of Security Keys
- 10 Reasons to Love Passwordless #6: The Passwordless Funnel
- 10 Reasons to Love Passwordless #7: Authenticator app for easy phone sign in
- 10 Reasons to Love Passwordless #8: You won't get phished!
- 10 Reasons to Love Passwordless #9: Onboard without a password
- 10 Reasons to Love Passwordless #10: Never use a password
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.