Cybercrime’s newest business model, human-operated attacks, emboldens criminals of varying ability.
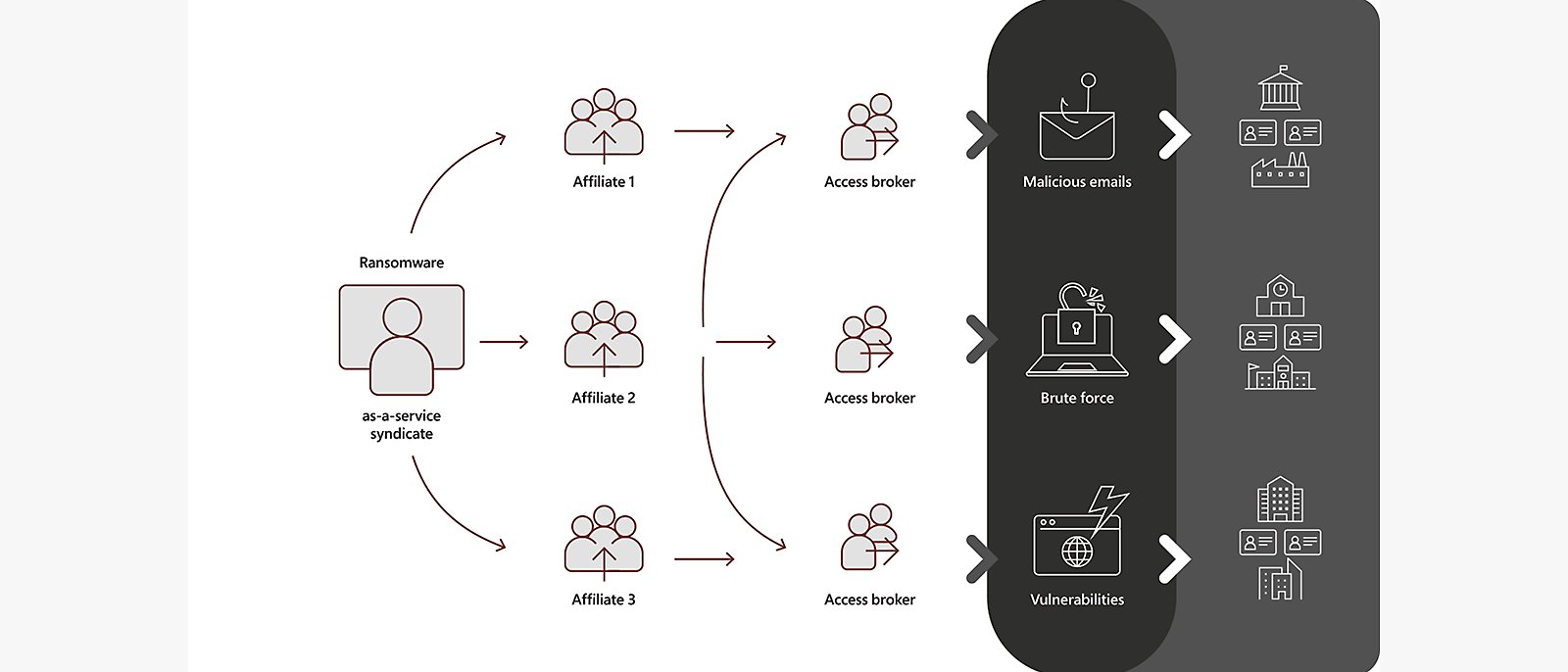
Ransomware, one of the most persistent and pervasive cyber threats, continues to evolve, and its latest form presents a new menace to organizations worldwide. The evolution of ransomware doesn’t involve new advances in technology. Instead, it involves a new business model: ransomware as a service (RaaS).
Ransomware as a service (RaaS) is an arrangement between an operator, who develops and maintains the tools to power extortion operations, and an affiliate, who deploys the ransomware payload. When the affiliate conducts a successful ransomware and extortion attack, both parties profit.
The RaaS model lowers the barrier to entry for attackers who may not have the skill or technical wherewithal to develop their own tools but can manage ready-made penetration testing and sysadmin tools to perform attacks. These lower-level criminals can also just buy network access from a more sophisticated criminal group that has already breached a perimeter.
Although RaaS affiliates use ransomware payloads provided by more sophisticated operators, they are not part of the same ransomware “gang.” Rather, these their own distinct enterprises operating in the overall cybercriminal economy.