1 Management Summary
The KuppingerCole Market Compass provides an overview of a market segment and the vendors in that segment. It covers the trends that are influencing that market segment, how it is further divided, and the essential capabilities required of solutions. It also provides ratings of how well these solutions meet our expectations.
This Market Compass covers solutions that enable Secure Collaboration, operating from a data-centric philosophy that allows the movement of data objects and files between users – internal or external – while maintaining highly secure protections on that data. This is a shift from purely restrictive protection like DLP solutions, or protective additions like encryption. While such solutions remain relevant, they transition to being supportive tooling or components of the more flexible, interoperable, and therefore even more secure solutions in the Secure Collaboration market space.
The market is still heterogenous, with many vendors offering a variety of solutions to address similar use cases. The major use cases for enterprise information protection include data-centric security, internal and external collaboration, audit and analytics, compliance, and modernization of data management. A strong solution is one that protects enterprise data with flexible access control that follows the data wherever it travels, triggered by data discovery scans, data classification and/or manual action. Encryption is typically used to protect data objects and files at rest, in transit, and in use, with robust key management capabilities. While this covers the security aspects, Secure Collaboration solutions must enable virtual collaboration. Instead of a prohibitive protection style, Secure Collaboration solutions should facilitate easy sharing of data with the right people in the right context. There must be close integration with commonly used collaboration platforms and workplace tools to minimize friction. Interoperability with identity providers and identity standards can enable single sign-on (SSO), federation, and other smooth authentication options.
KuppingerCole is covering technologies that are critical for companies to be successful in their digital transformation journey. Readers of this Market Compass will learn about the trends and developments in this market segment, be introduced to and compare the major vendors in this segment, and prepare themselves to identify their own requirements for a Secure Collaboration solution. Readers should consider vendors based on the internal requirements of their own organization's use cases and use this report as a guide to shortlist vendors.
Key Findings:
- Secure Collaboration vendors secure enterprise information for collaborative work within the enterprise and with partners, suppliers, customers, etc. while maintaining persistent protection.
- Through acquisitions, many vendors in the traditional information protection space are adding capabilities that facilitate better collaboration.
- Virtru is rated Outstanding in Innovation
- Microsoft is rated Outstanding in Functionality
- Exostar is rated Outstanding in Regulated Industry
- Secude is rated Outstanding in Extending Microsoft Purview Information Protection (MPIP) Functionality
- Micro Focus is rated Outstanding in Securing Structured and Unstructured Data
2 Market Segment
This Market Compass covers solutions that enable Secure Collaboration, operating from a data-centric philosophy that allows the movement of data objects and files between users – internal or external – while maintaining highly secure protections on that data. This is a shift from purely restrictive protection like DLP solutions, or protective additions like encryption. While such solutions remain relevant, they transition to being supportive tooling or components of the more flexible, interoperable, and therefore even more secure solutions in the Secure Collaboration market space.
This section provides the market description of Secure Collaboration solutions, the major use cases, and the direction this market is heading.
2.1 Market Description
Information is critical to business today. Information drives the modern economy, creating the base for business communication and processes, supplementing or being derived from products and services, containing mission-critical information or intellectual property, or as the input for analytics, automation, and digitization efforts. Information is exchanged as a part of daily processes or tasks, powering collaborative exchanges between coworkers, partners, suppliers, and clients. This exchange also proliferates the information, creating duplication, shadow stockpiles of sensitive data, multiple versions in various stages of completion, and ownership or access to data objects and files that cannot be accounted for. Before labelling these as security hazards, it should first be recognized that these realities often go hand-in-hand with virtual collaboration. Enabling virtual collaboration is often an essential step in digital transformation, and can only be done securely when data-centric protection facilitates secure collaboration.
To unlock the power and usefulness of enterprise data and to match the way business is conducted, it must be mobile, with accountable security as it moves and works for the organization. The context in which enterprise data exists has changed significantly. With the reality of a fast-fading organizational perimeter, the organization likely operates in a multi-cloud and/or multi-hybrid and "post-perimeter" age. Security of data in such an age cannot be bound to infrastructure when the infrastructure itself is agile. Internal relationships with the organization have likely changed with "work from home" employees, device sprawl, and Bring Your Own Device (BYOD) that offer many more locations, hardware, and mediums with which to access data. Efforts to manage and improve sourcing, logistics, supply chains, and partnerships require collaboration with many external partners, contractors, suppliers, and freelancers. The increasing usage of edge computing and non-human identities that produce, process, or consume data will add complication to the data protection question in the future. This shift in the way data exists and is used in and around the organization requires data to be mobile and facilitate collaboration.
Not only does information need to be mobile, it also needs to be secured. Organizations must ensure that their intellectual property is protected, as well as the many other data assets that they may hold including personal information, health information, copyright, or information restricted to certain audiences (trade secrets, some legal contracts, agreements, financial statements, etc.). Adherence to regulations such as NERC CIP, GDPR, CCPA, HIPAA, and many others may restrict the type of data that may be stored, the retention length, and reasons for storing data. Organizations will need to ensure that this data is seen only by a few select individuals, and need to control the actions that can be taken on it, and the environment in which it can be viewed. External and internal threats remain constant, even though the need to mobilize and collaborate using corporate-held information is increasing. Therefore, securing data and information has quickly climbed to a high-ranking priority in enterprises today.
These circumstances have given rise to the Secure Collaboration market segment. Vendors in this segment enable collaborative work within the enterprise and with partners, suppliers, customers, etc. in a secure manner. The focus of this report is on the vendor's ability to provide security for collaboration, and optionally secure collaboration tools.
The inclusion criteria that vendors met in order to participate are:
- Discover structured data in file shares, specific collaboration systems, cloud (IaaS and/or SaaS), etc.
- Discover unstructured data in the locations specified above
- Classify structured data (tool may add row/column/table for tracking cell-level sensitivity)
- Classify unstructured data (data objects such as documents, engineering drawings, binary files, source code, SML, JSON, etc. in endpoint and server file systems, document management systems, applications, etc., whereby metadata "tags" are added to individual data objects)
- Access control with policy-based authorization for document/information access to take action (fine grained: authorized users on trusted devices to read, edit, download, print, screenshot, etc.), with flexibility on the attribute types to be used in policies and examined at runtime (users, groups, roles, organizational affiliations, citizenship, clearances, contracts, etc.)
- Flexible and strong means of authentication and federation as precursors for authorization, such as Windows, FIDO, authenticator apps and SDKs, SAML, OAuth, JWT, etc.
- Encryption is essential for secure collaboration. This should be supported at the data object level at rest, in motion, and in use. Ideally it is based on policy with the option to be applied based on metadata tags, and at folder level/file level/metadata level
- Encryption key management, HSM support, etc.
- Enable collaboration, with preference for compatibility with Office365, Google Cloud, Slack, and other commonly used platforms and simplicity to make the solution work within the organization. The solution should also enable collaboration on documents, virtual teamwork, etc. within the organization and enable secure collaboration with external partners. Deployment of client-side components should be taken into consideration.
- For secure collaboration solutions, the need for convenient, user-friendly implementations that impose as little friction as possible when integrated with often-used tools and platforms (e.g. Office365) is essential.
The exclusion criteria is as follows:
- Solutions that predominantly offer collaboration tools without significant security capabilities such as simple file sharing solutions.
- Exclusively DLP or information classification solutions. Must have wider functionality.
2.2 Major Use Cases
Secure Collaboration solutions serve many purposes in an organization, with many potential use cases depending on the organization's needs. The main applications of this solution are:
- Data-Centric Security: With the blending and fading of the organizational perimeter, a data-centric security approach becomes more important. Securing the data where it resides and travels can handle the flexibility and dynamic nature of organizational structures, locations, devices, and changing relationships and privilege. This security is persistent, following the data wherever it travels and is used.
- Internal and External Collaboration: Organizations may focus on the fine-grained access control to data for particular file types, storage locations, or devices. Centralized policies may be triggered based on classification, or users may manually apply access policies to files and data. Leveraging directories and federation can allow identities to be associated with policies to allow internal and external collaboration.
- Audit and Analytics: Maintaining an audit trail of data object permissions, (un)authorized accesses, and actions taken is essential for most organizations. But hand in hand with the need to collect and export audit trails is the usefulness of collecting insights and performing analysis on organizational data, for example on its risk exposure.
- Compliance: Organizations across different verticals have varying compliance needs: GDPR, NIST, ITAR; EAR, DFARS, CCPA, SOX, FDA, HIPAA, and many others. Secure Collaboration solutions help address data sovereignty and residency questions, and can flexibly adjust to the requirements of the relevant regulations.
- Modernization: Shifting to hybrid cloud, cloud-native, and multi-cloud require the integration of new business applications, services, and IT structures, and a modern approach to security. Enabling a centralized approach for both legacy and new applications to manage secure data storage, sharing, and authorization is essential. Automation in discovery, classification, and triggering policy can reduce cost and effort.
2.3 Market Direction
The Secure Collaboration market is being shaped by several trends: More complex deployment environments with higher needs to flexibly collaborate, zero trust security approaches, and rising privacy compliance concerns all impact the direction that Secure Collaboration solutions will take.
The KuppingerCole Trend Compass shows how traditional information protection solutions, often disparate combinations of encryption, data loss protection (DLP), and digital rights management (DRM) still remained relevant, especially through the COVID-19 pandemic, but that Secure Collaboration solutions are rapidly maturing and gaining market share.
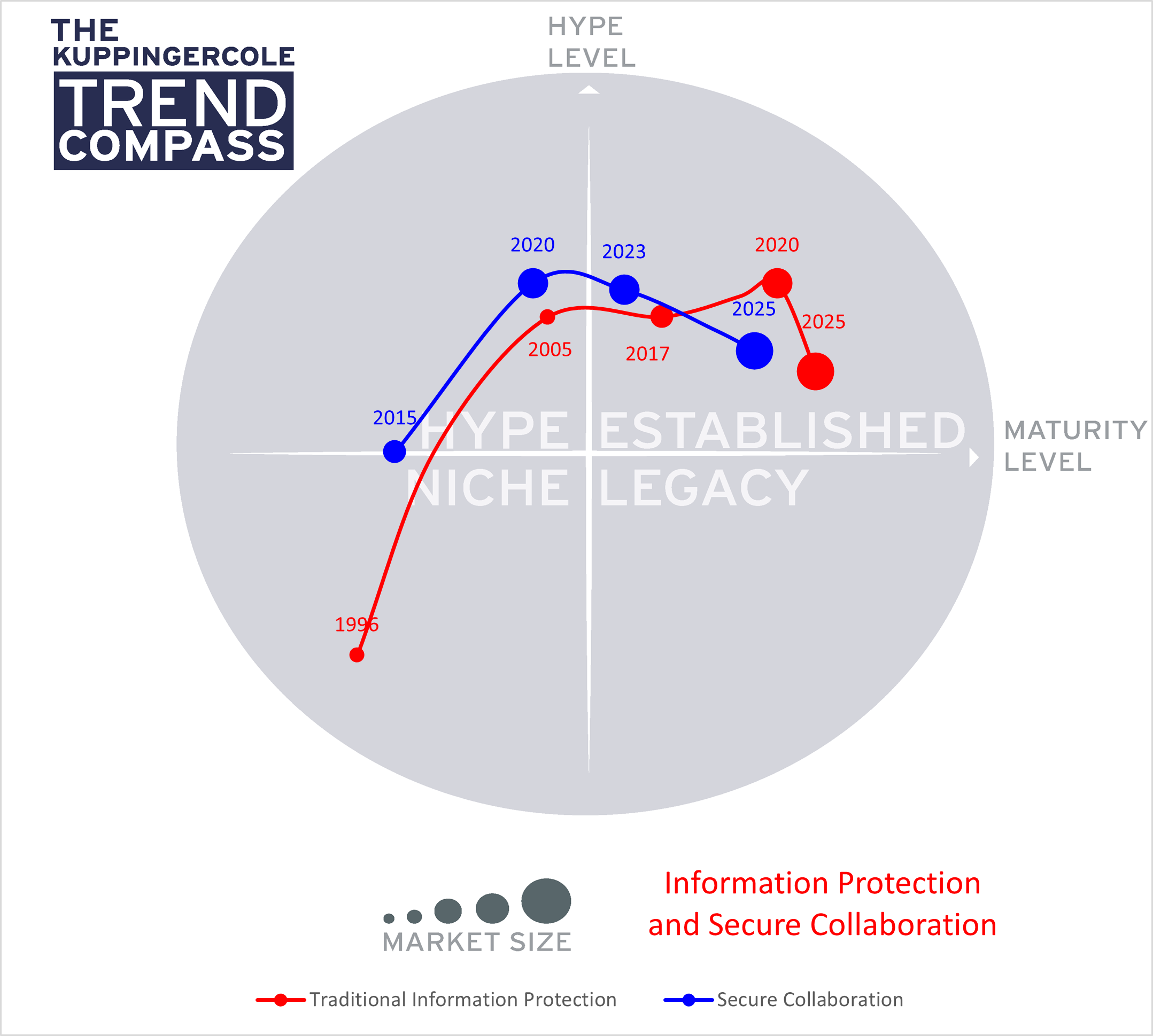
Traditional information protection solutions rose nearly to their peak in the mid-2010s, then saw a quick resurgence in 2020 with the onset of the global pandemic. However, it will likely see a decrease in hype in the next three years as the disparate information protection tools approach legacy usage and pivot toward providing Secure Collaboration Solutions.
Secure Collaboration solutions were already on the rise as the pandemic hit, causing a quick change in the location of workers, the flood of digitalization projects, and increased need to collaborate virtually with internal and external participants. Through acquisitions, many vendors in the traditional information protection space are adding capabilities that facilitate better collaboration. This, and the tendency to enhance or build off of existing technology stacks of collaboration platforms, causes the maturity of Secure Collaboration solutions to advance quickly. As traditional information protection solutions build out their collaboration capabilities, there will likely be a convergence of the blue and red trend lines.
3 Capabilities
The Market Compass is designed to profile and compare vendors across numerous capabilities. This section details the capabilities that one should expect to see in this market segment, and breaks them down according to relevance per use case.
3.1 All Capabilities
The Secure Collaboration segment has a collection of standard capabilities that most solutions should include. These are listed in the table below.
| Capability | Description |
|---|---|
| Unstructured Data Discovery | Identify the location of corporate data and parsing to identify categories of sensitive data such as PII. Sensitive data is often hidden in seemingly innocuous documents, databases, or even in messaging logs. Data discovery is an essential prerequisite for knowing what data must be protected when designing and enforcing security compliance policies. A foundation of data discovery also helps ensure that any access control policies in place are applied consistently across data silos and heterogeneous environments. |
| - For unstructured data | |
| - On-premise discovery for servers, web applications, and endpoints | |
| - Cloud discovery for IaaS-hosted apps, file shares, collaboration systems | |
| - Integration with methods such as DLP, CASB, Data Catalogs and Metadata Management | |
| Unstructured Data Classification | Assign a metadata label that indicates the sensitivity or classification of the data. Although classification of corporate data does not directly provide protection, it lays the groundwork so that access control policies can be applied and enforced. |
| - For unstructured data, a persistent metadata tag is added to individual data objects in file systems, chat logs, and collaboration platforms | |
| - Support for different types of data objects including all major file types and CAD files | |
| - Automated and manual functions that trigger access control policies | |
| Structured Data Discovery | Identify the location of corporate data and parsing to identify categories of sensitive data such as PII. Sensitive data is often hidden in seemingly innocuous documents, databases, or even in messaging logs. Data discovery is an essential prerequisite for knowing what data must be protected when designing and enforcing security compliance policies. A foundation of data discovery also helps ensure that any access control policies in place are applied consistently across data silos and heterogeneous environments. |
| - For structured data | |
| - On-premise discovery for servers, web applications, and endpoints, repositories, and databases | |
| - Cloud discovery for IaaS-hosted apps, repositories, and databases | |
| - Integration with methods such as DLP, CASB, Data Catalogs and Metadata Management | |
| Structured Data Classification | Assign a metadata label that indicates the sensitivity or classification of the data. Although classification of corporate data does not directly provide protection, it lays the groundwork so that access control policies can be applied and enforced. |
| - For structured data, may add row/column/table for tracking cell-level sensitivity | |
| - Support for different types of data objects including all major file types and CAD files | |
| - Automated and manual functions that trigger access control policies | |
| Access Controls | Control the access to and actions that can be taken on data through dynamic policies. Access controls ensure that data is not misused and that business operations that rely on it are not compromised. |
| - Dynamic and persistent policy-based management | |
| - Policies based on various data and/or user attributes | |
| - Prevents issuing excessive privileges | |
| - Fine-grained actions on data objects (read, edit, download, geo-fencing, etc.) | |
| Authentication | Users should authenticate themselves when accessing the management console and for users to access protected data. Multi-factor authentication (MFA) and/or single sign-on (SSO) are recommended. |
| - MFA | |
| - SSO | |
| - Support for contextual or adaptive authentication | |
| - Integration with directories and support for SAML, OAuth, OIDC | |
| Encryption | Provide enhanced protection of data and files through the appropriate encryption for the data's current state. This should protect it against theft, unauthorized access, and corruption. |
| - Protect data at rest through encryption of file systems and storage | |
| - Protection data in motion, during transfer of data. | |
| - Protection of data in use, such as viewing or editing a file | |
| - Support for email body and attachment encryption | |
| Key Management | Support secure storing, managing, and monitoring encryption keys. This should typically provide user control of encryption keys and Hardware Security Modules (HSMs) with the appropriate compliance and security certifications. |
| - User control of encryption keys | |
| - Key management with versioning, support for symmetric and asymmetric keys, encryption, decryption, signing, and verification | |
| - Internal or network-connected HSM | |
| - Full audit trail of key usage | |
| Virtual Collaboration | Products should add a layer of security that does not inhibit usual business processes, workflows, and daily tasks of employees and collaborators, particularly in virtual environments. Beyond simply "not inhibiting", Secure Collaboration tools should enable virtual teamwork. |
| - Secure collaboration products should integrate well with productivity/collaboration suites such as Office365, Google Cloud, Slack, and other commonly used platforms | |
| - Facilitate collaborative work on shared documents | |
| - Facilitate secure sharing of information through secure viewers, dynamic watermarks, etc. | |
| - Extend classification and protection policies to messaging channels, etc. |
Table 1: Standard Capabilities of Secure Collaboration Platforms
3.2 Capabilities Recommended per Use Case
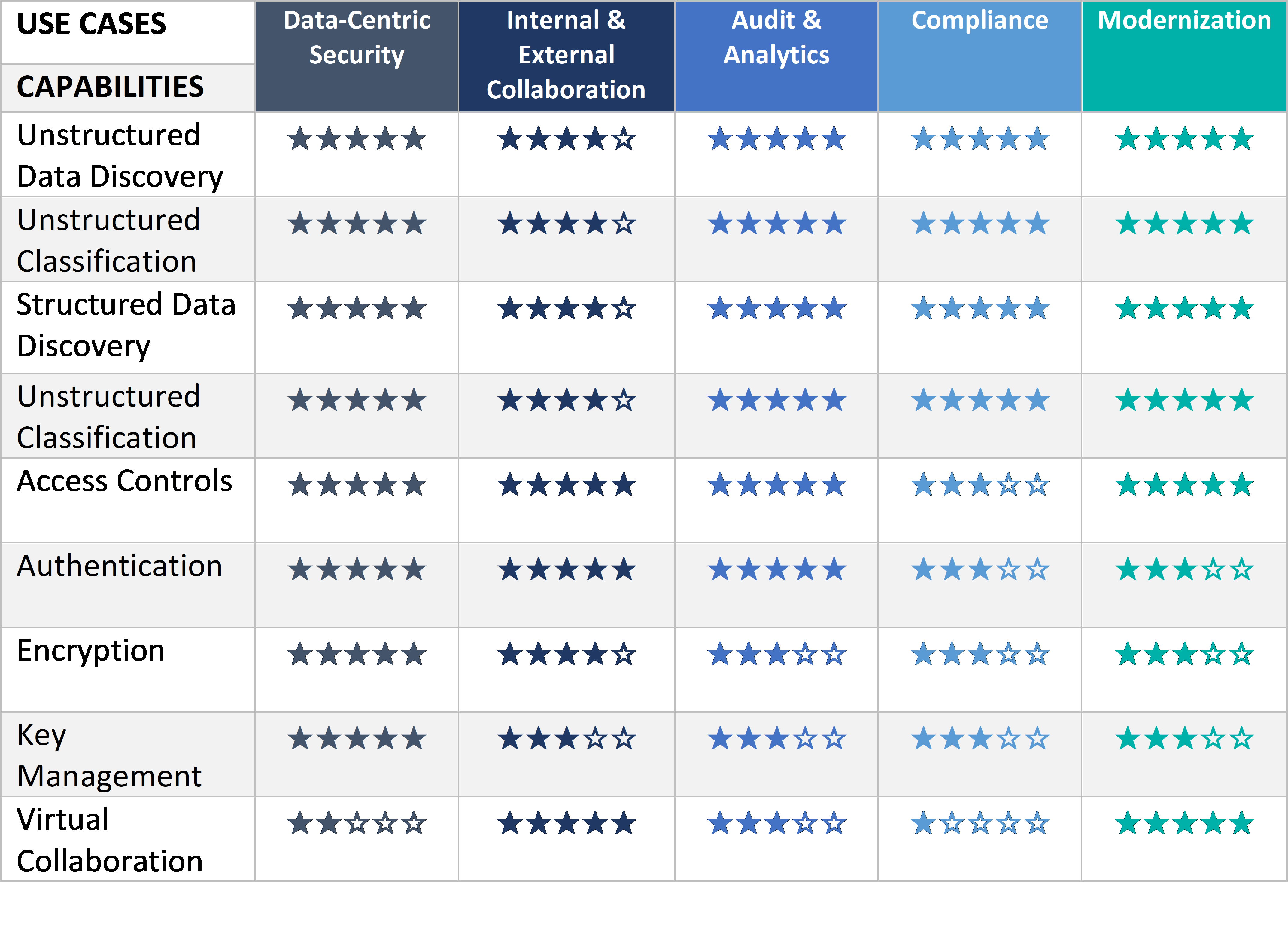
The Secure Collaboration segment is evolving to meet several distinct use cases, as described in section 2.2. Below, the capabilities are displayed according to their relevance for each use case.
3.2.1 Data-Centric Security
For this use case, security controls are essential, providing broad coverage of all data and file types for discovery, classification, and application of access controls. Authentication is a key security measure and can raise the protection with contextual or dynamic implementations. Encryption and key management are the foundation of data security at rest and in transit, and in advanced implementations also in use.
Virtual collaboration in this use case focusing on security becomes a secondary, nice-to-have feature in addition to data-centric security controls.
3.2.2 Internal and External Collaboration
To facilitate internal and external collaboration, inclusion of virtual collaborative features are essential to enable common collaboration platforms, communication, sharing, and synchronous work on data objects. Access controls and authentication are also highly relevant in order to permit the right access to the right users, whether they are internal team members or external users.
Data discovery and classification for structured and unstructured data often is the underlying trigger for automatic access policies and will likely be required. But the organization may choose which data types and tooling will best fit their needs. Encryption and key management are also highly recommended, but the level and degree of control the organization needs over storage and management of keys will depend on the organizational requirements.
3.2.3 Audit and Analytics
Maintaining audit trails and analytics depends on the information from access requests, actions taken, data discovery, and classification. Encryption and key management are supportive capabilities to deliver this use case. Virtual collaboration capabilities also do not directly advance this use case.
3.2.4 Compliance
Because there are so many different compliance requirements depending on the industry, region, and collaboration needs, the required capabilities for this use case remain very flexible. When privacy compliance is the top priority, discovery and classification are essential to knowing what private data the organization has, where it resides, and lays the groundwork for fulfilling DSARs.
Security or industry-related compliance may require strong authentication, close control and monitoring of access to IP or company secrets, and specify encryption and key management control.
Capabilities that integrate these security aspects with virtual collaboration increase usability, which indirectly advance the use case through higher adoption rates.
3.2.5 Modernization
For the modernization of data management between legacy and new applications, discovery, classification, and a powerful policy engine are essential. Intentionally building out virtual collaboration that interacts with centralized authorization policies is a key step in modernizing the data management and workflows of the organization.
While authentication, encryption, and key management are vital to security, they are not necessarily the most important when modernizing or centralizing data management.
4 Ratings at a Glance
This chapter provides a comparative overview of the participating vendors for five categories: security, deployment, interoperability, usability, and market standing. It also highlights outstanding performers in distinct categories.
4.1 General Product Ratings
Based on our evaluation, a comparative overview of the ratings of the general standing of all the products covered in this document is shown in the table below.
| Product | Security | Deployment | Interoperability | Usability | Market Standing |
|---|---|---|---|---|---|
| archTIS NC Protect |  |
 |
 |
 |
 |
| Exostar The Exostar Platform |  |
 |
 |
 |
 |
| HelpSystems Data Security Suite |  |
 |
 |
 |
 |
| Micro Focus Voltage Data Privacy and Protection |  |
 |
 |
 |
 |
| Microsoft Purview Information Protection Platform |  |
 |
 |
 |
 |
| NextLabs SkyDRM |  |
 |
 |
 |
 |
| SealPath IRM |  |
 |
 |
 |
 |
| Seclore Data-Centric Security Platform |  |
 |
 |
 |
 |
| Secude HALOCORE & HALOCAD |  |
 |
 |
 |
 |
| Virtru Platform |  |
 |
 |
 |
 |
| Zoho WorkDrive |  |
 |
 |
 |
 |
Table 2: Comparative Overview of the ratings for the general standing of all products
General product ratings do not measure the functionality of the product. For functionality ratings, see the spider graphs displayed per vendor in section 5.
4.2 Noteworthy Vendors for Specific Capabilities
Some vendors are better positioned to meet narrow use cases, while others have stronger offerings across the range of this market segment. We have identified a few vendors that are notable for their strengths for specific capabilities. A vendor has been selected as outstanding based on information collected during our neutral research and rating process.
4.2.1 Outstanding in Innovation: Virtru
Balancing collaboration and security is the status quo, but innovating in order to advance collaboration through the lens of security policies is the target. Virtru is making compelling steps in this direction with its Trusted Data Format (TDF), and secure file sharing space that enables each party to determine the access rights of the information they share.

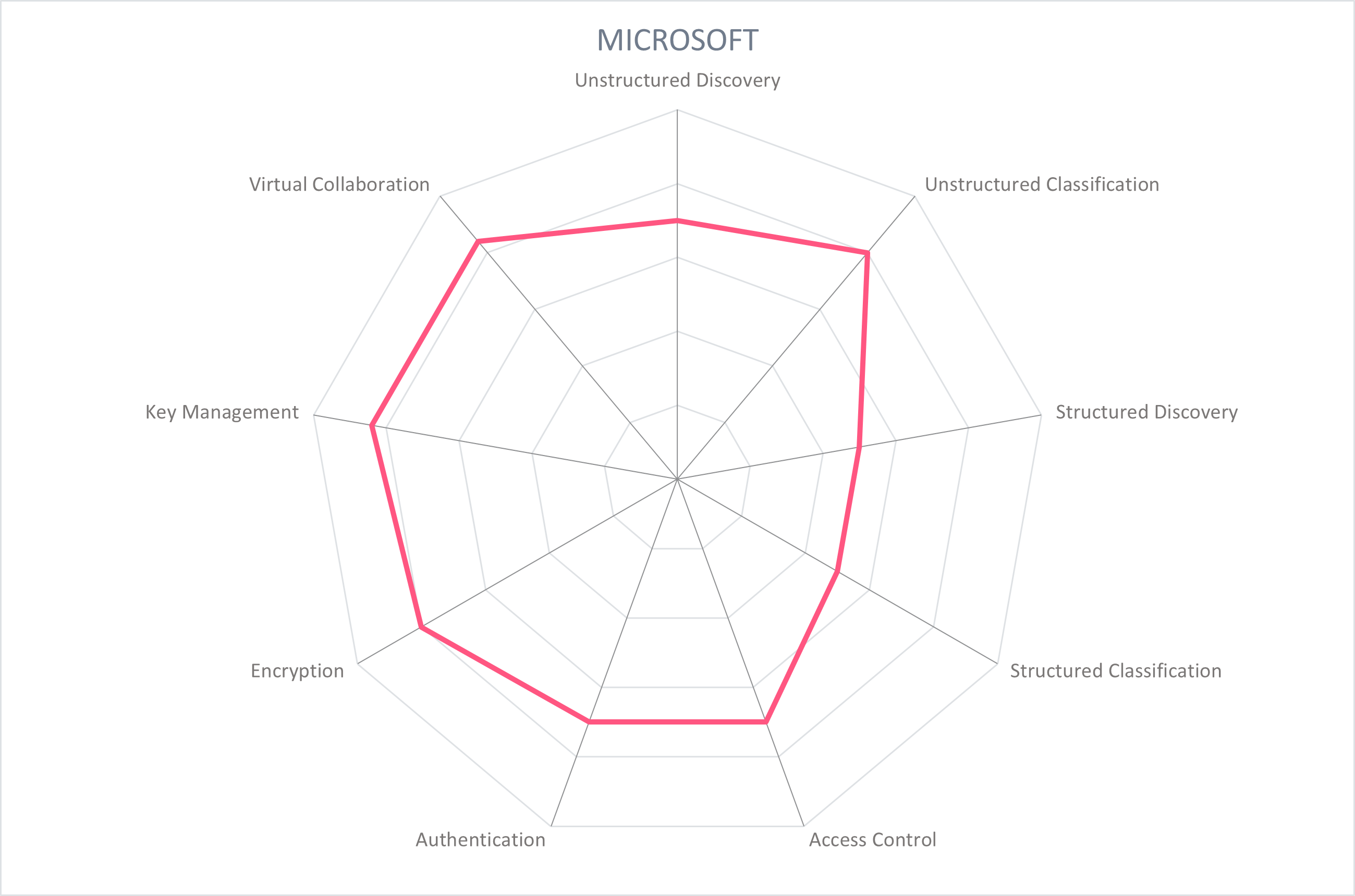
4.2.2 Outstanding in Functionality: Microsoft
Functionality includes both technical capabilities and the demonstrated effort to enable collaboration in a secure way without hindering the natural flow of work processes. Microsoft Purview Information Protection (MPIP)'s sensitivity labels and protection policies are embedded in often used collaboration tools, cover both structured and unstructured data, and invest in extending these capabilities to other digital collaboration channels such as Teams calls. Double key encryption can protect multinational organizations or those who need to maintain exclusive control over keys.

4.2.3 Outstanding in Regulated Industry: Exostar
Regulated industries have collaboration needs, but often face security barriers when working with suppliers, contractors, freelancers, or other third-party partners. Secure Collaboration solutions that specialize in serving the regulated industries enable cooperation while maintaining the highest levels of security and compliance. Exostar has cultivated a community of over 150,000 companies that are in the regulated industries or serve as suppliers and partners, facilitating smoother partner and supplier qualification, onboarding, and lifecycle and risk management between community members.

4.2.4 Outstanding in Extending Microsoft Purview Information Protection (MPIP) Functionality: Secude
Several vendors extend Microsoft Purview Information Protection for particular use cases, applications, or industries. Secude is one secure collaboration solution that addresses the secure use of PLM and SAP applications, expanding MPIP’s functionality to these environments for secure export, sharing, and collaboration.

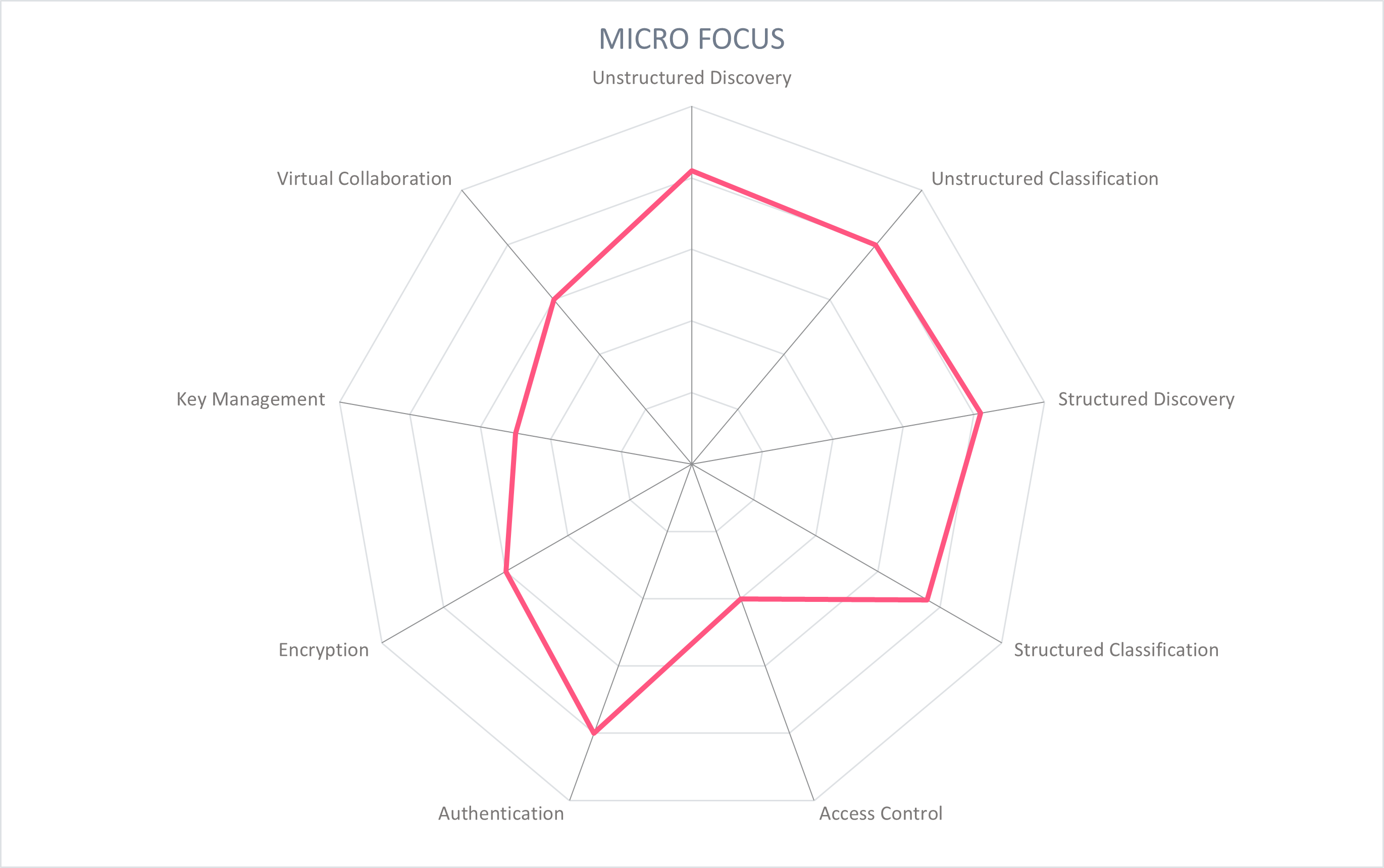
4.2.5 Outstanding in Securing Structured and Unstructured Data: Micro Focus
Protecting both structured and unstructured data sources with one solution can be challenging, and most rely on partners and connectors to implement full discovery and classification capabilities for both types of data. Micro Focus' Voltage Data Privacy and Protection provides discovery and classification for both structured and unstructured data sources, using its strong background in data discovery. It uses ML-based and context-aware analytics to identify sensitive and personal data, as well as gathering and displaying insights for remediation actions.

5 Product/Service Details
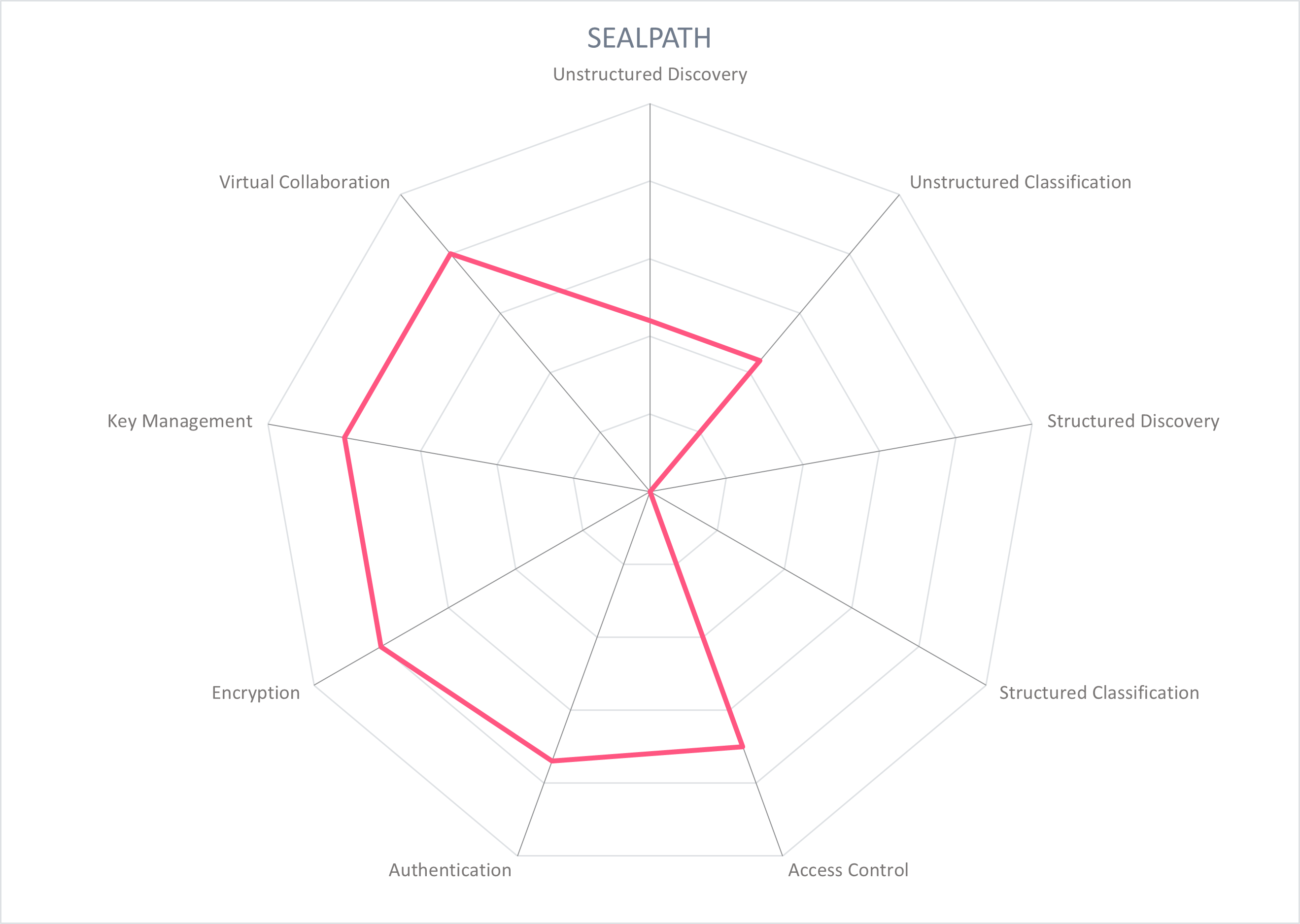
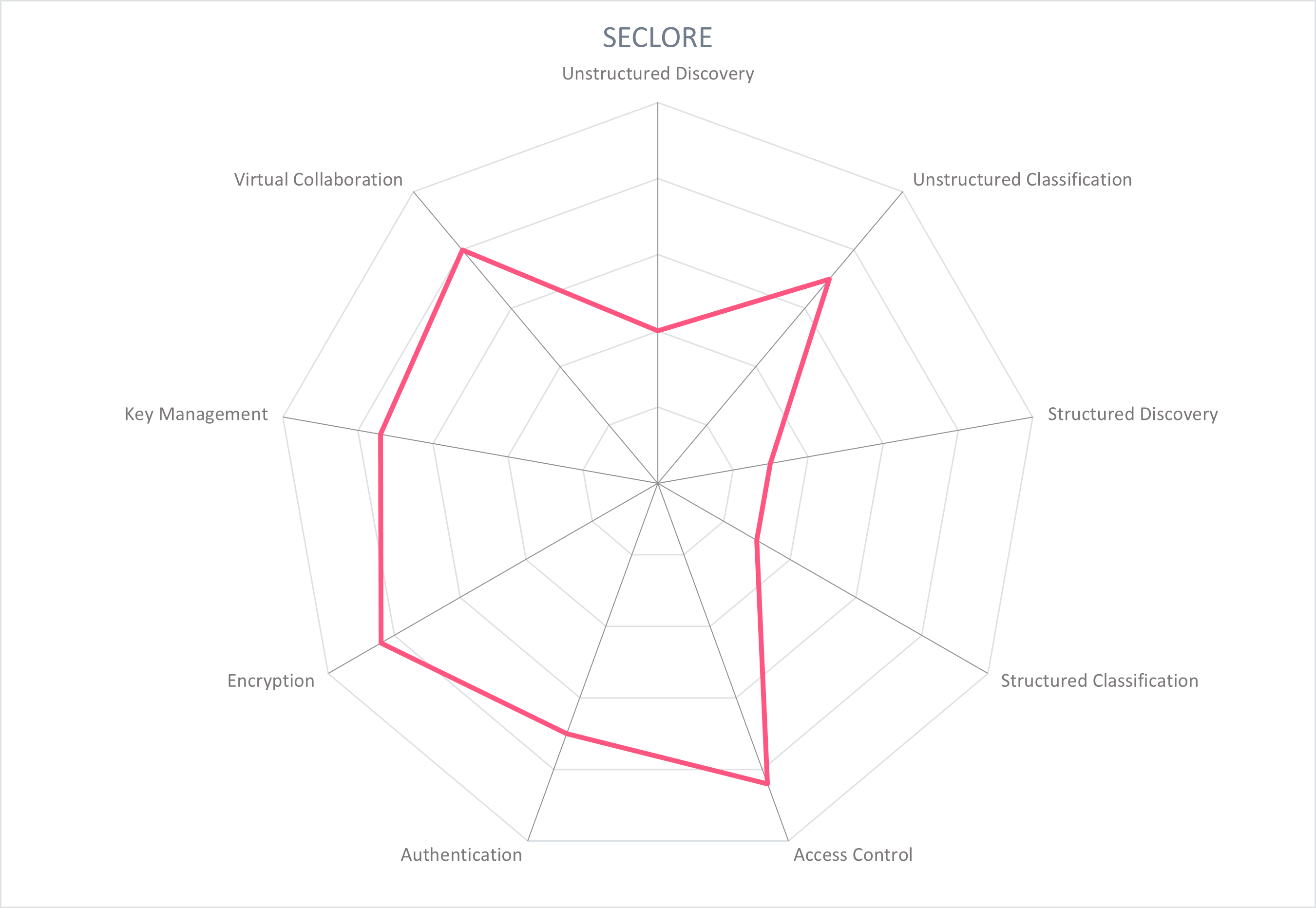
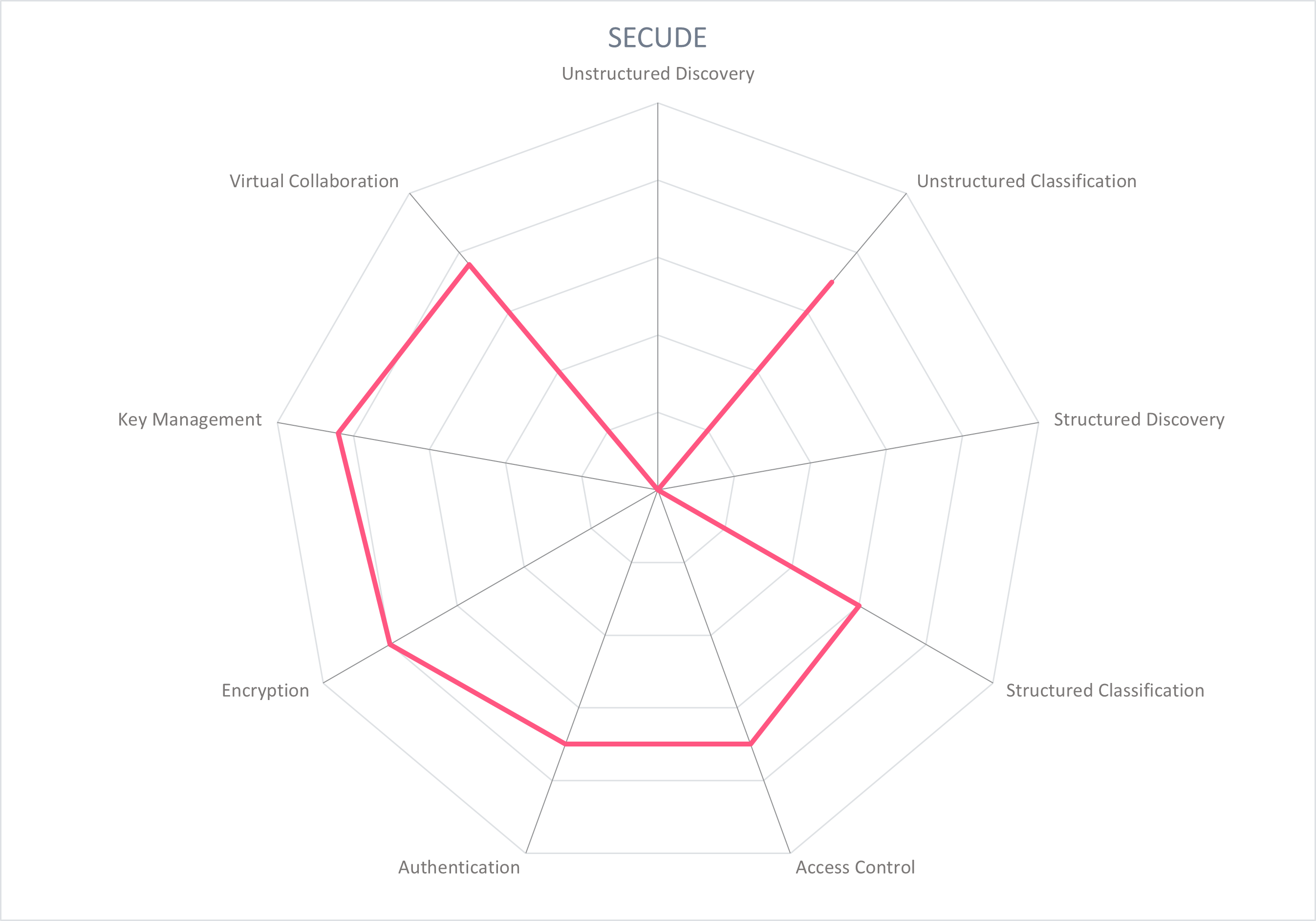
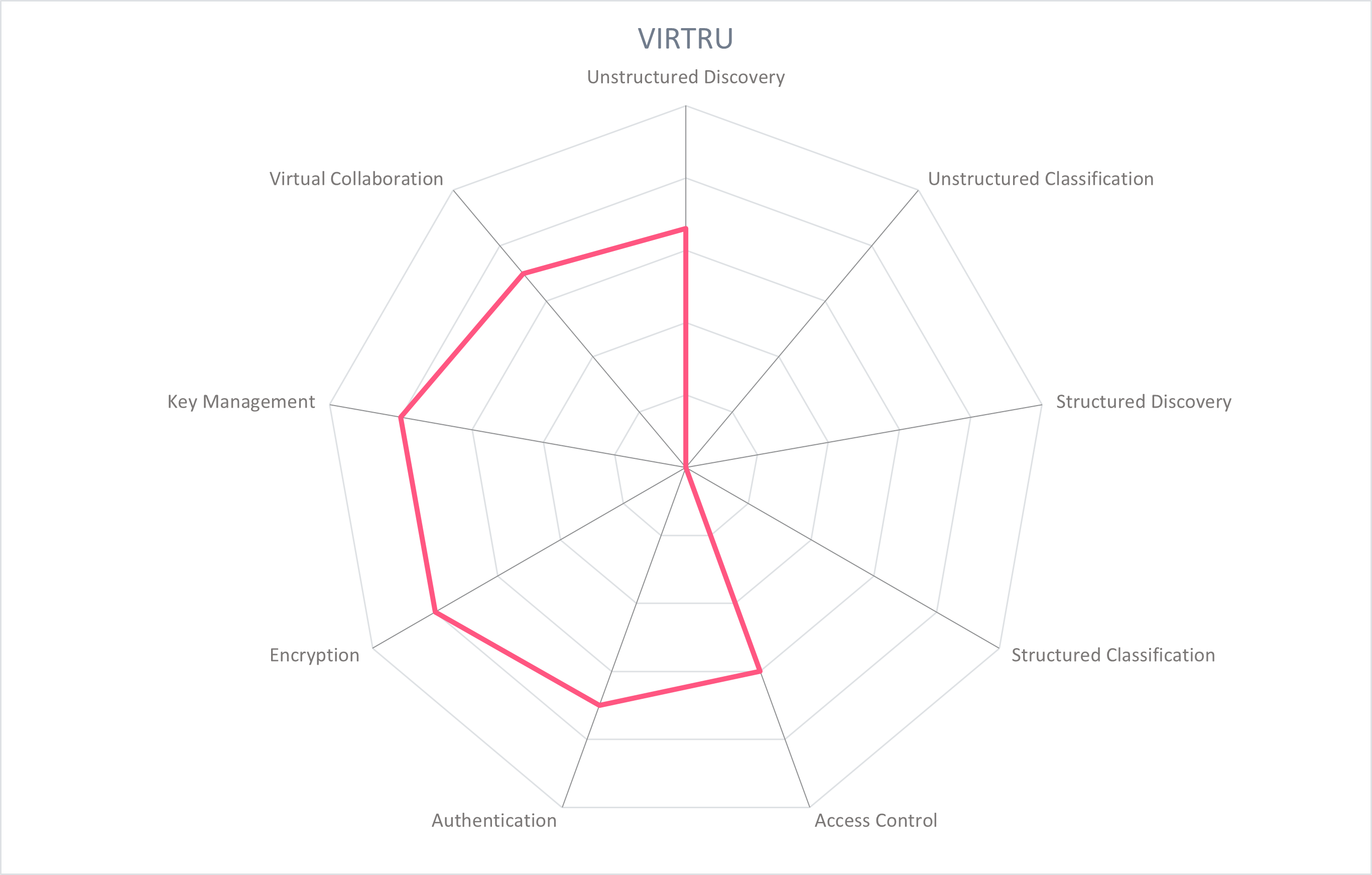
In the following section, each participating vendor is profiled with particular attention paid to the functionality of its product. Several important capabilities for providing Secure Collaboration have been selected and rated, displayed as a spider chart. For this Market Compass, we look at the following nine areas:
- Unstructured Data Discovery: Identify the location of corporate data and parsing to identify categories of sensitive data such as PII for unstructured data in cloud and on-premise locations.
- Unstructured Data Classification: Assign a metadata label that indicates the sensitivity or classification of the data in file systems, chat logs, and collaboration platforms, and triggers protection policies.
- Structured Data Discovery: Identify the location of corporate data and parsing to identify categories of sensitive data such as PII for structured data in cloud and on-premise locations.
- Structured Data Classification: Assign a metadata label that indicates the sensitivity or classification of the data in repositories and databases.
- Access Control: Control the access to and actions that can be taken on data through dynamic and fine-grained policies.
- Authentication: Users should authenticate themselves when accessing the management console and for users to access protected data. Multi-factor authentication (MFA) and/or single sign-on (SSO) are recommended.
- Encryption: Provide enhanced protection of data and files through the appropriate encryption for the data's current state.
- Key Management: Support secure storing, managing, and monitoring encryption keys. This should typically provide user control of encryption keys and Hardware Security Modules (HSMs) with the appropriate compliance and security certifications.
- Virtual Collaboration: Products should add a layer of security that does not inhibit usual business processes, workflows, and daily tasks of employees and collaborators, particularly in virtual environments. Beyond simply "not inhibiting", Secure Collaboration tools should enable virtual teamwork.
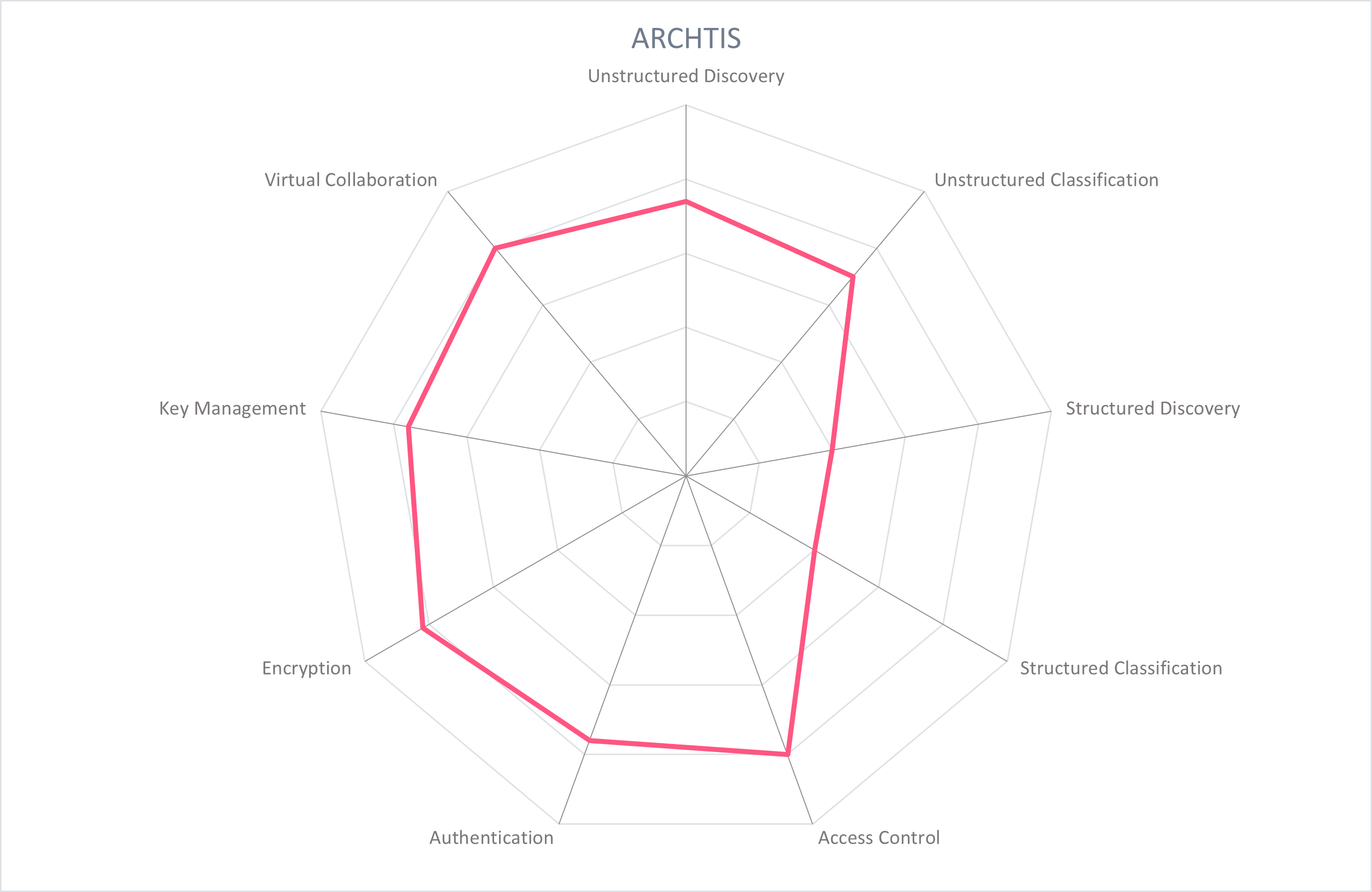
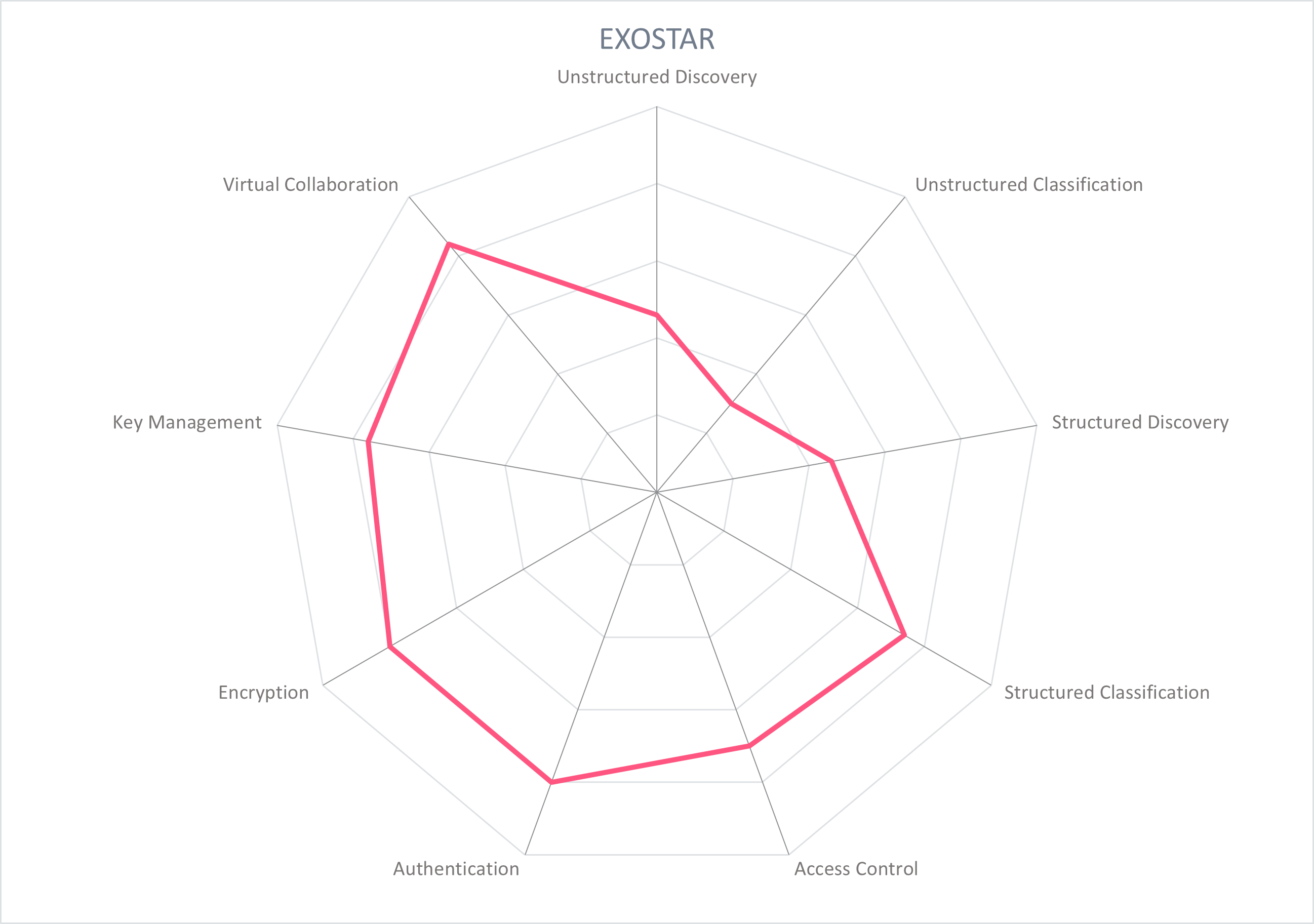
These spider graphs provide comparative information by showing the areas where the products are stronger or weaker. Some products may have gaps in some areas, while being strong in others. These might be a good fit if only the specific features are required. Other services deliver strong capabilities across all areas, thus being a better fit for strategic choice of product. The vendors presented in this Market Compass are strong performers, though none reach the highest possible score because of the anticipated technological advances we expect in the coming years.
5.1 archTIS - NC Protect
Founded in 2006 and based in Canberra, Australia, archTIS enables secure collaboration with a data-centric security approach. Its products, NC Protect and Kojensi, secure information with security policies that manage access to and actions taken upon data objects based on classification. This report focuses on NC Protect which is built on the Microsoft technology stack and interoperates with other key collaboration tools.
NC Protect leverages the Microsoft technology stack, giving it native integration with SharePoint online and on-premises, Teams, OneDrive, Yammer, Exchange, Windows File Shares, Dropbox, and Nutanix files. It offers the same core functionality with on-premises, cloud, or hybrid deployments. It is deployed within the SharePoint Service for on-premises deployments, and uses the Azure App Service for cloud deployments. It is available on the Azure Market place as of Q2 2022. NC Protect installs on the customer instance of Azure, meaning that data residency remains consistent with the customer's Microsoft deployment, running based on where the files are located.
NC Protect begins with file analysis to scan and discover sensitive information, classify and tag it, and enact dynamic access policies to protect files at rest and in motion. Audit logs are provided for reporting and monitoring. Discovering and classifying capabilities are for unstructured data, with support from partners to protect structured data. Files at rest and in motion are scanned for sensitive information, triggered by events such as file creation or edits to the file. File types that are supported include those supported by the Microsoft environment including all business documents (including Word, Excel, PowerPoint and PDF), Visio, emails, images (standalone and embedded in other file types (OCR)), text, CAD drawings, CSV, HTML, Teams chat, SharePoint contents within lists and libraries, and calendar events. Over 200 policies are available OOTB to identify and tag data including personally identifiable information (PII), cardholder data, protected healthcare data (PHI), intellectual property (IP), corporate confidential information, and more. Custom discover rules can be designed to use customer taxonomies, keywords, and pattern matching. One or more policies can be applied to documents with each policy result assigning a sensitivity label to restrict access and determine file protections. The product can also ingest Microsoft Purview Information Protection or other third-party metadata labels, or can be applied manually. Policies based on these labels dynamically apply protection and encryption to the file driven by the classification level.
Access control to each file is determined by policy rules that utilize the wide range of data attributes and combine and compare them to the attributes of the user, location, network, and device. This results in a dynamic access policy that determines the appropriate level of access and actions to take on that file, including what users can do with that file once access is granted, and who they can share it with. Depending on the policy, a file may be opened in a secure in-app or browser viewer for read only access, restricting copy, paste, save, download. Sensitive information is redacted or removed, and a dynamic watermark can be placed on files to dissuade screenshots or taking a picture with a mobile device. Files access can be restricted and are made invisible if the user does not have access, for example Teams channels or files are invisible to those who do not have access, or ribbon items in Office, SharePoint, and Teams are reduced to only permittable functions (copy, paste, print, download, etc.). Email body and/or attachments are encrypted, or can be automatically replaced with a secure link or be made to open in a secure reader, or may be blocked altogether.
NC Protect also identifies possible duplicates using content fingerprinting and presents its findings to an administrator. A master document can then be nominated and NC Protect will redirect all access of duplicates back to the master location.
Microsoft and archTIS have a close partnership, yielding the ability for NC Protect to natively ingest Microsoft Purview Information Protection (MPIP) sensitivity labels, along with other third-party sensitivity labels. Audit logs can be exported into Microsoft Sentinel, Splunk, or as a CSV file for reporting or event monitoring. Encryption at rest and in transit can be provided through Azure RMS, archTIS' own product NC Encrypt for customer-managed keys, or with Thales CipherTrust.
archTIS also developed Kojensi, a platform independent of other collaborative environments, and enables creation of, sharing, real-time document collaborating, and securing content, suitable for organizations that need secure collaboration across businesses, organizations, and/or departments that may not have the same tool set and/or have specific compliance requirements of their platform without potentially risky dependencies. Kojensi was not reviewed for this report.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.2 Exostar - The Exostar Platform
Founded in 2000 and headquartered in Virginia, Exostar provides a secure collaboration platform serving highly regulated industries including aerospace, defense, commercial aviation, government contracting, healthcare, life sciences, manufacturing, financial services, and insurance. Exostar has cultivated a community of over 150,000 companies in more than 175 countries, facilitating smoother partner and supplier qualification, onboarding, and lifecycle and risk management between community members. In addition to a stand-alone secure collaboration platform, Exostar can serve as a security enhancement built on top of an organization's existing collaboration platform, such as Microsoft Office 365, or as a managed service.
The Exostar Platform provides customers with an onboarding module, a secure access module, an applications module, and a business intelligence module. The onboarding module streamlines and accelerates the due diligence, certification, engagement, and recertification processes of partners and suppliers with checks on denied parties lists, financial health, and citizenship status (among many factors), incorporates a vendor master data model that defines and guides the gathering of data to meet an organization's fit-for-use qualification and compliance requirements for partners, and facilitates the completion and collection of forms and documents.
The secure access module provides a federated and/or SSO access gateway for enterprise employees, bolstered by in-person or remote identity proofing and credential issuance as necessary. Supplier access is supported with PKI and non-PKI methods, with the same proofing and credentialing options. The applications module includes a suite of secure collaboration applications for highly secure and compliant structured and unstructured cooperation. In the Exostar Secure Access for Microsoft 365 application, Exostar manages Office 365 tenants (sometimes in addition to the customer's own tenant, sometimes as a managed service option). The Exostar-managed tenant becomes the area for secure collaboration with use of Microsoft Teams and apps, with the ability to invite participants from the pre-vetted Exostar community. Secure access is enforced on internal and external Teams participants through user credentialing and strong authentication.
Exostar provides templates for different industries to support the team creation and user invitation processes. Classification labels can be selected during team creation. Internal and external members can be assigned with an email, lookup of own tenant members, or federate a domain through Exostar. As a governance mechanism, the external organization is first vetted, invited, and onboarded to the community before the individual external team member is admitted, with a full audit trail. Individual team members may be granted limited access or limited functionality in the Teams environment, based on the delegated administration of the asset owner.
Libraries and files are protected with a full Digital Rights Management (DRM) solution which incorporates technology from Seclore. SharePoint libraries are access controlled via policies that dynamically determine access rights on the basis of group membership or manually-granted permissions, with the option for step-up authentication. File entitlement policies such as print or download are attached to files which control access and usage rights of users. Policies can be modified to dynamically alter user permissions regardless of where the files may be stored, persisting if a file is sent as an attachment or downloaded.
To properly support a variety of regionally-created, globally applicatble regulatory security requirements, Exostar complies with the U.S. DoD DFARS 7012 (NIST 800-171) and the U.K. Official Sensitive & Cyber Essentials. Exostar is a Certification Authority, has been named a full-service credential service provider by the Kantara Initiative, and issues credentials based on the National Institute of Standards and Technology (NIST) 800-63 standard, Levels 1 through 4. Exostar is cloud server agnostic, supports over 60 file types, and supports all major operating systems and devices.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
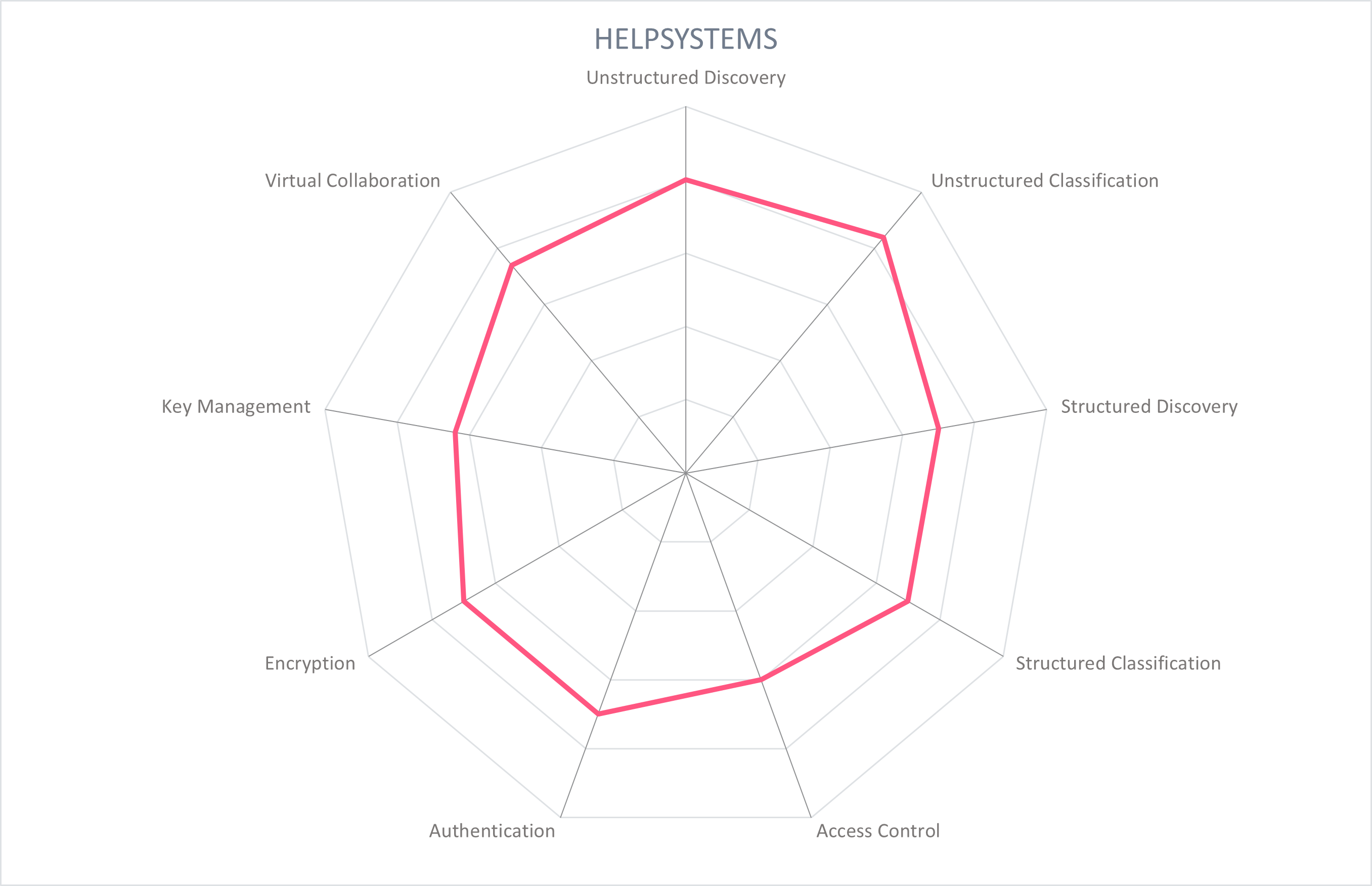
5.3 HelpSystems - Data Security Suite
Minnesota-based HelpSystems was founded in 1982. Through a series of acquisitions, it has assembled its Data Security Suite from the following brands: Titus and Boldon James for data classification, Vera for digital rights management, Digital Guardian for DLP, GoAnywhere, Globalscape, and FileCatalyst for secure file transfer, and Agari and Clearswift for email security. Capabilities from each brand compliment and extend the capabilities of the others, allowing HelpSystems to provide modular secure collaboration solutions to customers. HelpSystems is working towards deeper integration between their Data Security Suite brands.
The Data Security Suite covers data protection (with support for data classification, digital rights management, and endpoint DLP), secure file transfer (including managed file transfer and file acceleration), and email security (with brand protection, business email compromise (BEC), and secure email gateway). Beginning with determining what data is present in an organization, data discovery capabilities for structured and unstructured data are provided by Digital Guardian. Further discovery scans for unstructured data are performed by Titus, Clearswift Email Gateway, and GoAnywhere in combination with Clearswift ICAP Gateway. The results of the discovery scans are passed to classification solutions (Titus and Boldon James) for labeling, and/or Vera for DRM application. Data discovery capabilities cover endpoint and cloud-based apps and file shares.
Titus and Boldon James are the primary data classification brands for HelpSystems. Titus can either automate the assignment of classification labels to unstructured data, or enable manual classification supported by automated suggestions and recommendations on how to correctly label. Depending on the data type, labels are visible (O365 files, PDF) or in metadata (O365 files, PDF, AutoCAD, etc.). Boldon James supports manual classification, while Digital Guardian supports classification for structured and unstructured data in motion and at rest (in file shares, SharePoint, etc.) based on location of the data and the person or application accessing it for DLP purposes, or through automated discovery scans.
Automated or manual policy-based controls over data access rights stem from file classifications, provided by Vera. Protected files are encrypted, with key management handled by Vera. Policies – applied at the folder level and triggered by location, classification label, content detection or rules – provide control over what users with access to a file may do, including notification of access, edit, saving as a new file, printing, copy/paste, offline access, authentication, watermark, etc. Vera integrates with Box, Dropbox, SharePoint, SMB file shares, and most content management systems. Activity logging and Syslog integration is available. A protected file that has been shared opens either in app (when Vera is integrated) or when sent to an external, the file opens in the web browser. Digital Guardian also offers access control to files based on application, user, classification, and content, while Titus can restrict sharing based on AD attributes and group memberships.
HelpSystems' diverse secure collaboration offering allows customers to take a modular, requirements-based approach. Protection functionalities for external collaboration center around DLP and email protection, preventing sensitive information from being shared unnecessarily. This, in combination with Vera's digital rights management which restricts actions that can be taken on protected documents allow sensitive files to be shared with persistent protection.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.4 Micro Focus - Voltage Data Privacy and Protection
UK-based Micro Focus, founded in 1976, is a software company noted for its wide range of identity management, governance, and data products. Its data privacy and protection product Voltage Data Privacy and Protection is a union of two portfolios which began in 2020: discovery of structured and unstructured data, and data governance.
Data discovery is performed on both structured and unstructured data for endpoints, applications, databases, and file repositories. Different levels of scans can be conducted, including metadata scan, full scan, or a leaner "smart" scan. These scans can be deployed across the enterprise, or at a departmental level. Content analysis is performed to identify sensitive and PII data as defined by 39 different countries and economic regions. These data discovery actions serve as the input for further data analysis, protection, and governance actions.
Administrators have access to a dashboard to identify, analyze, and manage data sources in all locations: internal shared file systems, office-specific locations, cloud, or on-premise. The results of data scans are displayed with drill-down visualizations, including heat maps that indicate the location of high-risk data. Action can then be taken on this at-risk data, for example fulfilling a Data Subject Access Request (DSAR) by searching for an individual's personal data, visualizing it along with a timeline, by file type, tags, and level of protection. Searches can also be filtered by geographic location or type of sensitive information such as passport, phone number, etc. The dashboard provides a full audit trail of actions taken.
Protection policies can be set up based on the results of data scans, and deployed per type of information such as PII, credit card information, metadata tags, and so on. Protection is provided through patented masking and anonymization capabilities, for example with Format Preserving Encryption (FPE) for PII. Microsoft Purview Information Protection (MPIP) sensitivity labels can be ingested and used to trigger protection policies. Protection policies can also restrict who can view the data, such as only internal users, delete data, or archive it.
Voltage File Analysis can be deployed in public or private cloud, hybrid, or on-premise, with multi-tenant options.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.5 Microsoft - Microsoft Purview Information Protection Platform
Microsoft was founded in 1975 and is based in Redmond, Washington, USA. Among its wide offerings in hard and software is the Microsoft Purview Information Protection Platform (MPIP), a comprehensive solution to protect sensitive information. It follows a classify, label and protect process, and is built into Office apps, Office 365, and other MS services like Power BI, Teams, Edge, Windows, and Azure. Administrators use a single admin console for policy configuration and management across on-premise, Office apps, services, third-party services, and devices.
Microsoft Purview Information Protection provides a sophisticated classification system that can apply labelling to a document based on the creator, the context in which it was created, and/or the content within the document. The functionality is natively embedded into Office services and apps, and third-party applications via the MPIP SDK. Sensitive information is discovered and labeled with out of the box, custom, and machine learning (trainable) functionality. Information such as credit card, SSN, person names, licenses, and business categories like healthcare or financial can be classified out of the box. Custom fields include RegEx, Dictionary, Fingerprint, Named entities detection (e.g. person name, address, medical terms), Exact Data Match, and credentials. Based on policy, the discovery of this information can lead a file to be classified based on customer-defined schemas such as Public, General, Confidential, etc.. Manual, prompted, and automated classification mechanisms are supported. Customers get an onboarding experience that allows them to simulate their classification algorithms against real data in their production environment and fine-tune as required before deploying.
The management console allows administrators to create policies for security groups and set conditions such as "apply visual markings" to alert a user to a file's classification. Default labels and policies can be applied for the customer environment, including files, emails, groups, sites, and data assets in Microsoft Purview. Policies can also include encryption and usage restriction for files and emails, support BYOK and HYOK, and activate Double Key Encryption.
At the file level, creators of the file determine its classification either manually or as recommended by the classification engine. The file then carries this label and encryption which ensures it is protected for its lifetime. File permissions can be automatically triggered based on policy, including editing, copying, exporting, printing, forwarding, and allowing macros. File owners can track statistics on who has accessed their documents and revoke permissions if necessary. Classification policies connect with the data loss prevention module and carry out protection across the Microsoft environment, including in Teams chats. Conditional access to files can be enforced with multifactor authentication, IP address, location, etc.
Microsoft's device registration feature ensures network access from authorized devices – i.e., those that have been explicitly enrolled in the organization's list of mobile devices approved to access the network. The multi-factor authentication feature registers a personal device, usually a smartphone, to approved users and a message will be sent to the device as part of the login process to act as the "something you have" factor. Logging, auditing and reporting facilities are provided. PDF vendors including Adobe, Foxit, and Microsoft Edge PDF have built Microsoft Purview Information Protection labeling and protection capabilities within their reader products.
MPIP also supports on-premise products such as Exchange server, SharePoint Server, Windows file servers and other network shares that use SMB or NFS. The product provides built-in labeling and protection capabilities in Office on all platforms including iOS, Android, Mac, and web. Mobile devices (iOS and Android) are supported.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
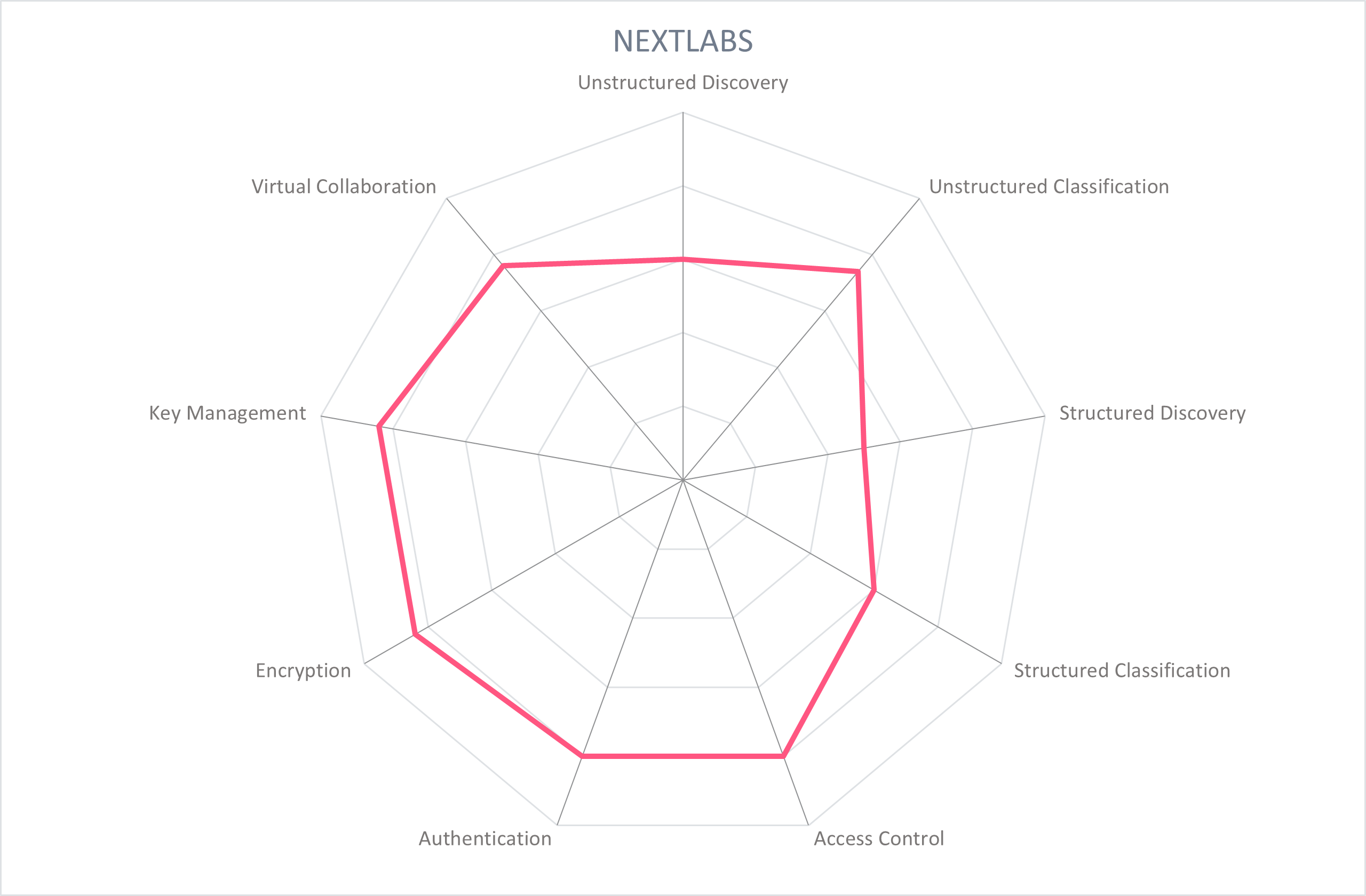
5.6 NextLabs - SkyDRM
Founded in 2003 and based in California, NextLabs provides dynamic authorization and access management software and services. Its data-centric security platform, SkyDRM, leverages dynamic authorization with ABAC policy control. From a beginning in the aerospace and defense industries, NextLabs' industry focus has expanded to health and life sciences, high tech, manufacturing, government, financial services, chemical, and energy market segments.
The NextLabs product offering, including SkyDRM, utilizes a policy management server for policy management, decision, distribution, and enforcement. The policies are defined and managed centrally based on customer business requirements. Policies are dynamically determined at the point of access by subject, environmental, and resource attributes, as well as by the action to be performed. Subject attributes include role, function, clearance, etc., and environmental attributes include geolocation, IP address, regular working hours, or device. Resource attributes like data classification or application classification are supported with an automatic database scan, classification, and application of protection policies based on rules. Files can also be manually classified by the user at the time of creation or sharing. This metadata is stored with the file in an encrypted container, and travels with the file where it is stored, sent, or used. SkyDRM policy can work across multiple domains.
SkyDRM provides OOTB integration with leading applications including SAP, PLM, Google Suite, and Microsoft 365. SkyDRM Desktop enables any 3rd party application to access files protected by SkyDRM. It is also interoperable with search, record retention, discovery, archiving, and AV tools. The product supports SAP, Siemens, Google Suite, Adobe, and Microsoft file types, as well as video, image, text, source code, and 2D and 3D CAD models by SAP Visual Enterprise, Siemens NX, Dassault CATIA and SolidWorks, PTC Creo, and Autodesk AutoCAD. Protections can be applied at the file, application, and database level. Unstructured data is protected at the file, application, and database level, with dynamic authorization policies applied when the dataset is exported into an unstructured format, for example a PDF. When a file is shared with a user, the user's authentication triggers a dynamic authorization decision with the actions that may be performed if access is granted, including view, edit, print, save as, extract, add a dynamic watermark, prevent screenshot, or add an expiration date.
SkyDRM can be deployed as a SaaS, managed service, or be run on a customer's own private cloud or on-premise, in which Docker-based containers could be used. It is cloud-native with a containerized architecture suitable for on-premises, multi-cloud, or hybrid cloud. SkyDRM is supported on web browser, Windows, iOS Linux and Android. Customers can use SkyDRM's key store or bring their own key, with functionality to work with any KMS via KMIP protocol. SkyDRM supports federation from most identity providers using SAML or OAuth, identities can be sourced from AD, AzureAD, or any OIDC and LDAP-compliant directory, and supports Single Sign-on. Not all SkyDRM users need to install its client software, and users can access or view the file in the web browser or with the native business application. Audit trails are created with every action or reproduction of the document, monitored by the dynamic rights management server. SkyDRM also provides mobile support through its iOS and Android app.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.7 SealPath - SealPath IRM
SealPath was founded in 2010 and is based in Spain with a presence in several EMEA countries (Portugal, Poland, UAE, and Turkey) and partners in more than 25 countries. Its main product, SealPath IRM, provides enterprise rights management solutions that work in an integrated manner with a variety of DLP solutions, classification, cloud, and document management systems with a focus on improving usability, collaboration, and protection automation. SealPath IRM automatically secures information stored in file servers, document management systems, and cloud collaboration tools at rest and in motion, and includes protection for emails and attachments.
SealPath layers encryption, access control, revocation of rights, and auditability to protect files and enable collaboration. Using a concept they call Circles of Trust, policy-based permissions are applied for groups of internal and external users using Active Directory or LDAP groups. Administrators and leaders of the "circle" can manage their own policies independently of IT admin to take advantage of the business knowledge that determines the best protection of documents. These users can restrict access for other group members, define their permissions, share protected files with other collaborators and external users, and more.
Protected files are visually marked with an antennae icon to indicate their status. Rights management can be applied to MS Office, PDFs, images, text, and industrial formats like CAD (including AutoCAD, Inventor, Siemens SolidEdge, Dassault Systèmes Catia, SolidWorks, DraftSight, ARES, and others). These file types are encrypted and protected in transit, in use, and at rest. Rights that can be managed include view, edit, copy and paste, print, and the ability to add users. Additional control and protection features include expiry dates, dynamic watermarks, and revocations per policy, user, group, IP/subnet, domain, and file/document. Revocation of access and rights is possible at any time. SealPath also offers plugins of its Security Sandbox technology for CAD for MPIP customers to protect and control CAD files in different formats.
When integrated with classification and/or DLP tools, SealPath IRM can automate the implementation of these policies based on scans or ingested metadata tags, resulting in i.e. automatic protection of files with credit card information or GDPR-protected information. These permissions follow documents regardless of their location or method of sharing (including Google Suite, SharePoint, email, or USB), and persists offline.
Collaboration is enabled with self-sign-up procedures for external users. Protected documents can be opened in the native app, or users can work with collaboration tools like Office 365 or SharePoint directly in the browser without needing to download the document to the desktop. All standard devices and operating systems are supported, and includes the option to use a browser version instead of a downloaded client.
Administrators can review the audit trails of all protected documents as well as statistics such as documents with the most risk, the top ten active users or documents, and so on. All actions on a file are logged for audit and reporting purposes. Security is bolstered by enabling customer key management when needed, protected by an HSM. SealPath IRM can work with identity management systems or with privilege accounts management tools through its integration with AD and LDAP.
SealPath IRM can be installed on a customer's servers on-premises with customer-managed keys with HSM, be deployed as a SaaS, or particularly for MSPs. No agents are required to use with the enterprise's usual tools such as Office 365, Adobe, AutoCAD, and Outlook.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.8 Seclore - Data-Centric Security Platform
Founded in 2010 and headquartered in Milpitas, California, Seclore is a mature enabler of secure collaboration. Its Data-Centric Security Platform encrypts and secures files and email communication with policy-based access controls for protection at rest, in transit, and in use. Seclore provides connectors to solutions such as data classification, DLP, and CASB offerings, creating a single dashboard for a holistic approach to securing enterprise information wherever it travels or resides – inside or outside of the organization.
Seclore secures the existing enterprise systems with its Unified Policy Manager sitting on-premise, in the cloud (via AWS) or with hybrid deployments. The policy manager integrates and connects with several types of security products like DLP, data classification, CASB, and SIEM for a unified dashboard view, auditing functions, and coordinated policies for rights management. The rights management for files consists of four general factors, controlling who can access the information, what actions they can take with the information, when they can access it, and from where. The policy engine can be classification driven, with classification tags mapped to policies. Microsoft Purview Information Protection (MPIP) sensitivity labels (as one example) can be ingested and taken into account by the policy engine. Protection is applied automatically or manually, with a centralized policy server allowing an administrator to define policies or allow individuals users to create their own policies to simplify the process to assign granular permissions for internal and external users (e.g ad hoc collaboration). With the O365 integration for example, an agent is installed on the endpoint and pushed out to the relevant apps, where the user selects the "protect with Seclore" option in the ribbon when creating a file. Or automated protection is applied at the file library level by the library owner.
To view a file protected by Seclore, no agent or plugin is required. External users can access protected files via any browser or by downloading the Seclore-Lite agent (no admin rights required) to access the file. If the user does have the Seclore agent (e.g. internal user), the file will open in its normal app. If the user does not have a Seclore agent (e.g. external user), it will open in a secure reader in the browser after the user authenticates (compatible with AD, SAML, and OAuth, with support for MFA and OTP). Depending on the policy applied, there may be a dynamic watermark with the user's credentials to discourage screenshots, read only, editing capabilities, and downloading enabled or disabled. A security widget will appear listing the rights available to the user.
Seclore provides unique policy federation, applying the policy that is associated with the file in its original location. If the file originated in SharePoint, the policy applies the assigned member or guest rights even when the file has been moved out of SharePoint. With policy federation, this protection applied at the file level persistently follows the document everywhere, including being sent as an attachment or being downloaded outside of the organization. Protected documents can be shared with internal and external users. Modifying a user's permissions within SharePoint will change the behavior or access rights to a document outside of SharePoint, including the complete revocation of access (e.g. off-boarding an employee).
Seclore has connectors or is OEMed technology with several collaboration platforms, including Microsoft O365 (SharePoint, Teams, OneDrive, Outlook, Exchange), Axway Syncplicity, Dropbox, Box, IBM Filenet, Dfin, DataSite One, EthosData, Firmex, Transperfect, STASH Global, HighQ, and SAP. Files are encrypted in motion and at rest. Full rights management that controls the actions that can be taken on a file as well as who, when, and where is available for 64 file types, and file protection that controls who has access to a file, when, and where is available for all other file types, including CAD drawings.
Seclore's focus on wide functionality and security make it a strong provider of secure collaboration products. It offers out-of-the-box connectivity with Enterprise AD or LDAP corporate directory services. It also offers a built-in user repository for managing external users, if required. Users logged into the corporate infrastructure enjoy SSO to the Enterprise Digital Rights Management service. Seclore authentication can also integrate with Microsoft Azure, Okta, Ping Access and Google ID services. Seclore key management is server-based, encrypting individual documents via a tamper-proof mechanism. Clients can utilize their own HSM for key generation. All major operating systems, devices, and file types are supported.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.9 Secude - HALOCORE & HALOCAD
Secude was founded in 1996, and is headquartered in Lucerne, Switzerland. Its products extend Microsoft Purview Information Protection (MPIP) for SAP (product HALOCORE) and CAD (product HALOCAD). As a long-term collaborator with SAP and Microsoft, Secude has deep knowledge on how to incorporate MPIP for SAP and CAD, which is not covered by MPIP's classification, labeling, and encrypting capabilities.
HALOCORE (MPIP for SAP) and HALOCAD (MPIP for CAD) protect data and files in SAP and CAD environments, for example when files are downloaded, exported, checked out for editing, or shared with suppliers. In both products, the security profile of the hosting application or data repository is transferred to that protected data and/or file leveraging MPIP. In the HALOCORE or HALOCAD server, the process metadata from SAP and/or Product Lifecycle Management (PLM) is mapped to MPIP labels for all exports, downloads, and during file check-out. These are implemented with add-ons or plugins.
In order to leverage MPIP for SAP, HALOCORE maps SAP's security controls using attributes and usage controls (for example usernames, T-codes, etc.) to the MPIP sensitivity labels. These labels are applied automatically and trigger a protection policy upon download, export, and M2M/API data streaming. Based on the user's SAP security and access profile of the data, HALOCORE's classification engine – sitting in the customer's on-premise or cloud IT infrastructure – determines the actions that must be applied for the file, for example read-only access. This is done automatically without any action from the user. Classification and protection are automatically assigned to SAP data exports for controlling SAP data exports. HALOCORE is an add-on, and is integrated with SAP S/4HANA for on-premise, private cloud, or hybrid deployment.
HALOCAD extends MPIP labelling and protection to CAD and Product Lifecycle Management (PLM) applications covering vendors like Autodesk, Dassault Systemes, Siemens, Bentley, and PTC. HALOCAD automatically protects check-outs and/or exports fromt he PLM systems. It applies the appropriate MPIP label based on the lifecycle without user action required. The assigned classification is a visible informational marking in the CAD application's ribbon menu. Pre-established policies determine which users have which access to protected documents, which require authentication with Microsoft credentials. Restricted privileges can be applied to files and users so that files may be read-only, may be edited by certain users, and more.
Both products are available in the Microsoft marketplace, and can be deployed on-prem, in the cloud, or in any hybrid model that the customer uses. The products can be deployed on most server OS including Windows and Linux variants, or orchestrated and deployed as containers with Docker. The products run exclusively in the customer's IT environment, with no software operated in Secude's environment. HALOCORE is device and platform agnostic. Secude provides a compelling offering for organizations already using MPIP and who rely on the secure sharing of files and data in SAP and CAD applications.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.10 Virtru - Virtru Platform
Virtru was founded in 2012 and is based in Washington D.C., USA. Virtru aims to enable a Zero Trust architecture for enterprises that facilitates secure data sharing. This is primarily done through email and Google Suite plugins and Microsoft Outlook Add-ins to provide object-level encryption and persistent rights management on files.
Virtru provides secure collaboration with any party (inside or outside the organization) through the use of data-centric security with end-to-end object-level encryption for data at rest, in motion, and in use, and enabling multi-party policy. It uses the Trusted Data Format (TDF), a data-agnostic protective wrapper for the data object, its metadata, encryption information, and payload. The encryption is bound to fine-grained attribute-based access control (ABAC). The protection is persistent, traveling with the data object through email, applications, file sharing, and collaboration tools.
Virtru encryption for email and attachments can be enabled by an administrator for enterprise-wide encryption based on sensitive information detection, or manually with a toggle switch in the email app. Actions which can be taken on an email and attachment are defined, including disabling forwarding, downloads, authentication to access, and expiration date. All rights and access to encryption keys can be changed or revoked after the email is sent. Dynamic watermarking as an additional protection can also be added. When the recipient receives the email and has a Virtru integration, the email automatically decrypts in the email client. If the user does not have a Virtru integration, the user must authenticate (with Google, Office 365, OT verification link, or with Virtu credentials) and is sent to a secure reader in the browser to read the email, view attachments, and reply.
The Virtru platform takes a data owner-first approach, allowing the data owner to set policy for data to enable multi-party control. Admins have the option to configure rules to trigger encryption, define types of attachments, custom text patterns, or build out own custom rules. These rules trigger a DLP service, or recommendations to inform and educate users that they are sending confidential information. Virtru integrates with the multiple DLP vendors. The platform has an external audit policy engine, maintaining independent records from the Google Cloud environment.
To share files not as email attachments, users share a link to their personal secure storage in Virtru's platform with collaborators. Virtru has zero knowledge and access to the data stored in a personal secure storage. Collaborators can upload files to this location, and collaborate on files that they have access rights to. Each party, even collaborators that are non-Virtru customers, controls the access rights and revocations to the files they upload. The platform supports large files. File uploads can be accompanied by both encrypted and unencrypted messages to the other parties.
Virtru is a SaaS offering, with on-premise options. Single sign-on is provided through Okta and other major vendors. Virtru is natively integrated in Google Suite and Salesforce, including email client plugins for Gmail and Outlook, a plugin for GoogleDrive, encryption for Google Cloud and Google Workspace. Emails and attachments from SaaS apps such as Salesforce and Zendesk are protected with a Data Protection Gateway, and file sharing (sending and receiving) can be facilitated through a secure link.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
5.11 Zoho - WorkDrive
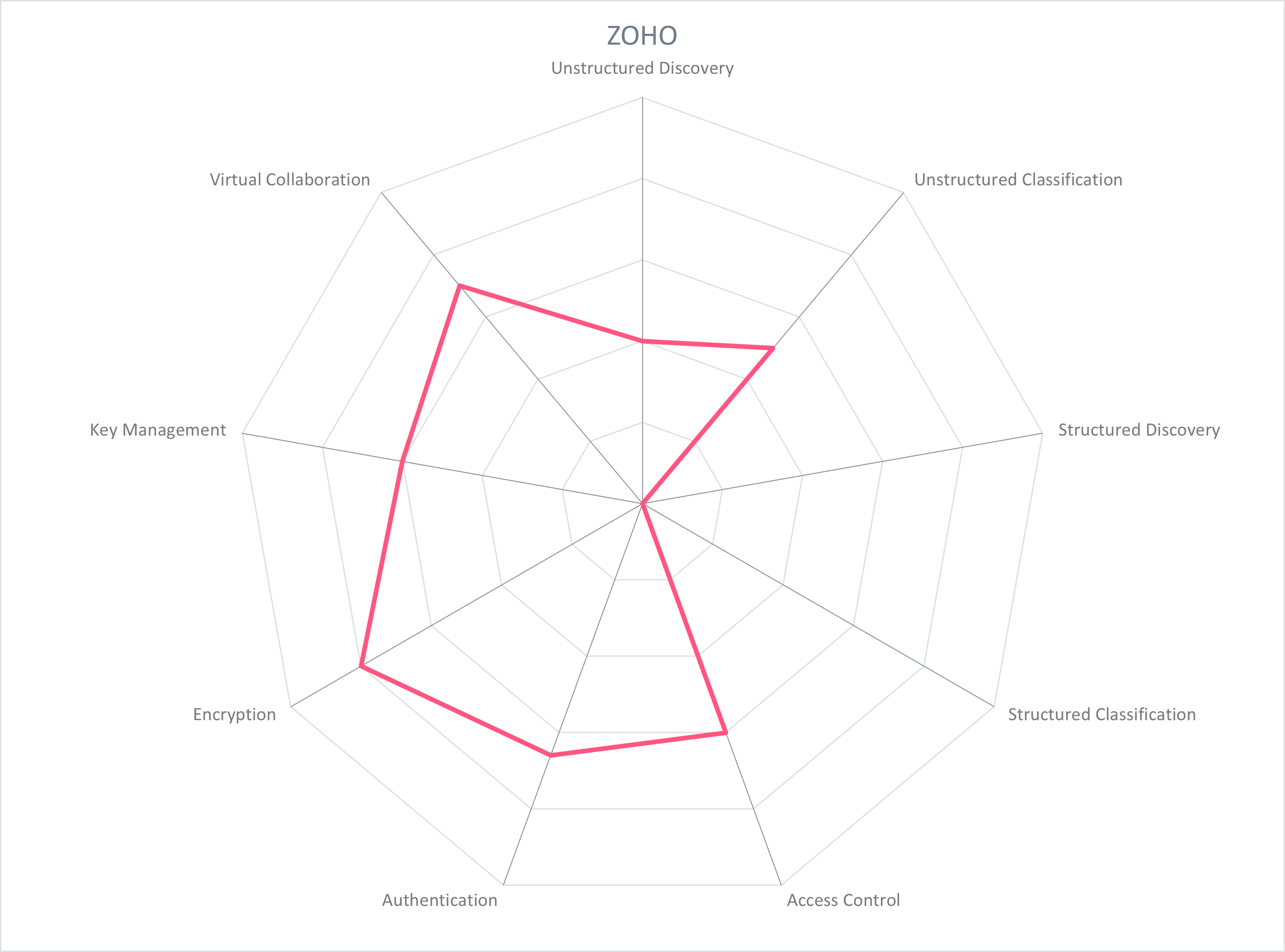
Zoho was founded in 1996 and is headquartered in San Francisco, USA. Zoho provides a suite of over 50 applications for business productivity, collaboration, and analytics. Its productivity platform, WorkDrive, aims to help businesses create a central and unified file storage. It provides both the productivity tools and file access control features to enable secure collaboration.
The WorkDrive platform is comprised of integrations with other Zoho products, like Zoho Projects, Zoho Office Suite, Zoho Sign, etc. which yields an environment for enterprise and SMB employees to create, store, share, and manage content. Role-based access control to folders and files enforce limited access to information for both internal and external users, and encryption protects files at rest and in motion. Auditing, analytics, and oversight are managed from an administrative console.
From the administrative console, administrators can create functional groups of internal members to reflect departments, projects, and so on. These groups, and individuals within them, can be assigned roles and rights to take action on files shared within that group. These roles include Admin, Organizer, Editor, Viewer, etc. The actions that can be taken on a file include view only, editing, sharing, and downloading. When a file is created or uploaded to a WorkDrive folder, the file owner can also define the team members or external users who can access the file as well as the fine-grained actions that can be taken. The file can be assigned a metadata tag, either customized or based on OOTB templates. Currently, these tags do not trigger automatic protection policies, nor integrate with external classification solutions. WorkDrive supports over 220 file types including MS Office Suite and Google Suite, which are converted to Zoho Suite file types and metadata tags are applied.
File sharing with external users is facilitated by sending a link of the encrypted file, with options to make access password protected, with an expiration date, view only, permit downloads, or to request user data such as name and email. File sharing with external users can also be managed by inviting the external to participate in a teams folder for a defined period of time by issuing a temporary license. Files are encrypted at rest and in transit. Zoho has in-house key management services to create, store, and manage keys across all Zoho services.
Users can be added and authenticated to the platform by importing email addresses or linking AD with SAML, OpenID Connect authentication and options for Single Sign-On. Support for in-house authenticators such as OneAuth and third-party authenticators such as Google Authenticator are provided. Audit trails can be accessed and viewed from the administrative console, including activity reports on specific files with uploads, edits, downloads, and previews. File versioning can be used for enforcing an authoritative copy, comparing changes, or restoring previous file versions. File search can be conducted across the platform and in Zoho's email offering, and includes keywords, creator, file name, OCR, and object detection for images. Data centers are owned and operated by Zoho with locations in Amsterdam and Dublin. WorkDrive is suitable for both enterprises and SMBs.

| Ratings | Security |  |
| Deployment |  |
|
| Interoperability |  |
|
| Usability |  |
|
| Market Standing |  |
| Strengths |
|
| Challenges |
|
6 Vendors to Watch
Besides the vendors covered in detail in this document, we observe some other vendors in the market that readers should be aware of. These vendors do not fully fit the market definition, but offer a significant contribution to the market space. This may be for their supportive capabilities to the solutions reviewed in this document, for their unique methods of addressing the challenges of this segment, or may be a fast-growing startup that may be a strong competitor in the future.
- AceroDocs is a 2016 startup based in Madrid, Spain. Its flagship product of the same name protects files as they are shared internally within the enterprise as well as externally.
Why worth watching: This is a user-friendly option for secure unstructured data sharing. - AODocs is based in Atlanta, Georgia, USA, and provides secure content services to control access to shared documents and maintain privacy compliance.
Why worth watching: AODocs is closely integrated with the Google Drive platform, and can be considered if your organization relies on this toolset. - AWS is based in Seattle, WA, USA. Its product Amazon WorkDocs is a secure file storage and content collaboration tool for organizations.
Why worth watching: AWS provides a managed service for secure content creation, storage, and collaboration. - Brainloop offers a complete package with data store encryption, dual key, rights management integration with workforce tools.
Why worth watching: Brainloop provides specialty products for confidential projects, covering the needs of enterprises in regulated industries. - Conpal is based in Neu-Isenburg, Germany, and provides data-centric protection, encryption, and authentication. Its products support several operating systems and mobile devices.
Why worth watching: Its combination of encryption and authentication for different platforms can be a compelling option for organizations. - Duality is based in Newark, New Jersey, USA and is a secure collaboration platform, powered with machine learning to collaborate on data sets while they are still encrypted.
Why worth watching: This is a cutting-edge approach to maintain confidentiality and privacy while actively working with data. - Egress was founded in 2007 and is headquartered in London. It provides data security services and enterprise information protection, particularly for email and file sharing.
Why worth watching: With its focus on email protection, Egress protects the organization from incoming malicious content and prevents outgoing data leakage. - Enveil is a data security company at the intersection of privacy and data governance, offering technical measures for collaboration on private information such as multiparty computing, homomorphic computing, and trusted execution environments.
Why worth watching: the overlap of data security, data privacy, and collaboration may mean that this vendor fits unique enterprise requirements. - Fasoo was founded in 2000 and is headquartered in South Korea. It provides a suite of products to protect unstructured enterprise data, including the data-centric policy enforcement aspect.
Why worth watching: Fasoo uses discovery and classification to support its rights management solution for unstructured data, making it a compelling solution for the enterprise. - Google is based in Mountain View, California, USA, provides its collaboration platform Google Drive.
Why worth watching: This is an often-used resource for enterprise and small-medium business collaboration. - Hyker Security is based in Malmö, Sweden and offers end-to-end security for the data lifecycle.
Why worth watching: Boasting zero-knowledge encryption and confidential processing, Hyker is an innovative option for privacy-conscious organizations. - Intralinks was founded in 1996 and is a financial technology provider for the global deal-making, alternative investment, and capital markets communities. It offers a SaaS multi-tenanted secure, document-centric collaboration solution.
Why worth watching: Intralinks serves a particular use case – M&As. This should be a consideration for organizations making deals. - M-Files was founded in Finland and is a content management system using a strong metadata approach to organizing and protecting content.
Why worth watching: M-Files offers high levels of automation for classification, setting permissions, and versioning. - MimeCast, headquartered in London, United Kingdom provides products that protect digital communication, with a focus on email and messaging security, and security enhancements for other collaboration platforms.
Why worth watching: Mimecast's Secure Email Gateway (SEG) and Mimecast Cloud Archive products serve as the foundation for its Collaboration Security Platform (CSP) for secure communication and collaboration capabilities. - ProofPoint, based in California, is a cloud-based, classification solution. It classifies and protects information according to industry pre-defined policies, and provides encryption for email services.
Why worth watching: ProofPoint provides analytics capabilities and visibility into data to gain insight into risk and take action. - Prot-On, founded in 2010 and acquired by Groupo CMC in 2017, is an information rights management solution for both the enterprise and the individual, with internal and external access control management. It also provides secure document collaboration services.
Why worth watching: Prot-On serves many different sectors, including financial services, legal, pharmaceutical, insurance, and the public sector. - Rhode & Schwarz Cybersecurity, based in Munich, Germany, provides a Cloud Data Protection Gateway for data residency, encryption, and compliance.
Why worth watching: Rhode & Schwarz can enable organizations to store sensitive data in their own data centers while still using collaboration platforms. - Thales, based in France provides cloud-based security for data protection, with elements of data discovery and classification.
Why worth watching: Thales has a proven track-record of work in regulated industries. - Treasure is a privacy-forward option that links collaboration tool accounts, provides client-side encryption, and enables secure file sharing.
Why worth watching: Treasure is a consumer-focused option that could work for small-medium businesses as well. - Tresorit, based in Zürich, Switzerland, provides secure file synchronizing and collaboration for businesses.
Why worth watching: With a focus on compliance, usability, and cloud-based, Tresorit can be a promising option for organizations. - uniscon was founded in 2009 and is based in Munich Germany. Its information protection services is deployed from uniscon's proprietary secure cloud. It operates a secure document storage facility and incorporates a rights management approach for in-use document protection.
Why worth watching: As a trusted cloud provider, uniscon takes a slightly different approach to delivering secure collaboration. - Varonis is based in New York, and provides a classification tool that identifies and protects sensitive data in files. It is supported by machine learning to monitor user access and recommend when access rights should be reduced.
Why worth watching: Predictive recommendations can be a good way to educate your team on secure data sharing habits. - Veza is a startup providing data-centric security through authorization and identity-data graphs to view, manage, and analyze permissions and access to data.
Why worth watching: A startup exiting stealth mode with enterprise customers could provide a new and different approach.
7 Related Research
Market Compass: Enterprise Information Protection - 80217
Leadership Brief: Enterprise Information Protection - 71036
Blog: Information Rights Management Explained
Executive View: Exostar Supplier Risk Management - 79074
Executive View: Micro Focus Data Protector - 80193
Executive View: NextLabs Data Centric Security in the Hybrid Cloud - 72531
8 Methodology
8.1 About KuppingerCole's Market Compass
KuppingerCole Market Compass is a tool which provides an overview of a particular IT market segment and identifies the strengths of products within that market segment. It assists you in identifying the vendors and products/services in that market which you should consider when making product decisions.
While the information provided by this report can help to make decisions it is important to note that it is not sufficient to make choices based only on the information provided within this report.
Customers must always define their specific requirements and analyze in greater detail what they need. This report doesn’t provide any recommendations for picking a vendor for a specific customer scenario. This can be done only based on a more thorough and comprehensive analysis of customer requirements and a more detailed mapping of these requirements to product features, i.e., a complete assessment.
8.2 Product Rating
KuppingerCole Analysts AG as an analyst company regularly evaluates products/services and vendors. The results are, among other types of publications and services, published in the KuppingerCole Leadership Compass Reports, KuppingerCole Executive Views, KuppingerCole Product Reports, and KuppingerCole Vendor Reports. KuppingerCole uses a standardized rating to provide a quick overview on our perception of the products or vendors. Providing a quick overview of the KuppingerCole rating of products requires an approach combining clarity, accuracy, and completeness of information at a glance.
KuppingerCole uses the following categories to rate products:
- Security
- Deployment
- Interoperability
- Usability
- Market Standing
Security is primarily a measure of the degree of security within the product/service. This is a key requirement. We look for evidence of a well-defined approach to internal security as well as capabilities to enable its secure use by the customer, including authentication measures, access controls, and use of encryption. The rating includes our assessment of security vulnerabilities, the way the vendor deals with them, and some selected security features of the product/service.
Deployment is measured by how easy or difficult it is to deploy and operate the product or service. This considers the degree in which the vendor has integrated the relevant individual technologies or products. It also looks at what is needed to deploy, operate, manage, and discontinue the product / service.
Interoperability refers to the ability of the product / service to work with other vendors’ products, standards, or technologies. It considers the extent to which the product / service supports industry standards as well as widely deployed technologies. We also expect the product to support programmatic access through a well-documented and secure set of APIs.
Usability is a measure of how easy the product / service is to use and to administer. We look for user interfaces that are logically and intuitive as well as a high degree of consistency across user interfaces across the different products / services from the vendor.
Market Standing is a measure of financial strength and market position. This is based on publicly available information, and takes the amount of funding received, the profitability, and the private or public status of the vendor into consideration.
We focus on security, deployment, interoperability, usability, and market standing for the following key reasons:
- Increased People Participation: Human participation in systems at any level is the highest area of cost and the highest potential for failure of IT projects.
- Lack of excellence in Security, Functionality, Ease of Delivery, Interoperability, and Usability results in the need for increased human participation in the deployment and maintenance of IT services.
- Increased need for manual intervention and lack of Security, Functionality, Ease of Delivery, Interoperability, and Usability not only significantly increase costs, but inevitably lead to mistakes that can create opportunities for attack to succeed and services to fail.
KuppingerCole’s evaluation of products / services from a given vendor considers the degree of product Security, Functionality, Ease of Delivery, Interoperability, and Usability which to be of the highest importance. This is because lack of excellence in any of these areas can result in weak, costly and ineffective IT infrastructure.
8.3 Rating Scale For Products
For vendors and product feature areas, we use a separate rating with five different levels. These levels are:
- Strong positive: Outstanding support for the subject area, e.g. product functionality, or security etc.)
- Positive: Strong support for a feature area but with some minor gaps or shortcomings. Using Security as an example, this could indicate some gaps in fine-grained access controls of administrative entitlements.
- Neutral: Acceptable support for feature areas but with several of our requirements for these areas not being met. Using functionality as an example, this could indicate that some of the major feature areas we are looking for aren’t met, while others are well served.
- Weak: Below-average capabilities in the area considered.
- Critical: Major weaknesses in various areas.
9 Copyright
© 2024 KuppingerCole Analysts AG all rights reserved. Reproduction and distribution of this publication in any form is forbidden unless prior written permission. All conclusions, recommendations and predictions in this document represent KuppingerCole's initial view. Through gathering more information and performing deep analysis, positions presented in this document will be subject to refinements or even major changes. KuppingerCole disclaims all warranties as to the completeness, accuracy and/or adequacy of this information. Even if KuppingerCole research documents may discuss legal issues related to information security and technology, KuppingerCole does not provide any legal services or advice and its publications shall not be used as such. KuppingerCole shall have no liability for errors or inadequacies in the information contained in this document. Any opinion expressed may be subject to change without notice. All product and company names are trademarks ™ or registered trademarks ® of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
KuppingerCole Analysts support IT professionals with outstanding expertise in defining IT strategies and in relevant decision-making processes. As a leading analyst company, KuppingerCole provides first-hand vendor-neutral information. Our services allow you to feel comfortable and secure in taking decisions essential to your business.
KuppingerCole Analysts AG, founded in 2004, is a global, independent analyst organization headquartered in Europe. We specialize in providing vendor-neutral advice, expertise, thought leadership, and practical relevance in Cybersecurity, Digital Identity & IAM (Identity and Access Management), Cloud Risk and Security, and Artificial Intelligence, as well as for all technologies fostering Digital Transformation. We support companies, corporate users, integrators and software manufacturers in meeting both tactical and strategic challenges and making better decisions for the success of their business. Maintaining a balance between immediate implementation and long-term viability is at the heart of our philosophy.
For further information, please contact clients@kuppingercole.com.











































