Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- How Microsoft EMS can support you in your journey to EU GDPR compliance – Part 1
How Microsoft EMS can support you in your journey to EU GDPR compliance – Part 1
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 08 2018 10:11 AM
18.3K
Views
Sep 08 2018
10:11 AM
Sep 08 2018
10:11 AM
First published on CloudBlogs on May 24, 2017
Hi everyone, By now most of you will, at the very least, have heard of the GDPR, the EU’s new law for data protection. GDPR stands for General Data Protection Regulation . Simply put, it aims to protect personal data from potential abuse. As Microsoft’s Chief Privacy Officer, Brendon Lynch mentioned in his blog “ The new General Data Protection Regulation (GDPR) is the most significant change to European Union (EU) privacy law in two decades ”. Today, I’m kicking off a blog series which will frame how we think Microsoft Enterprise Mobility + Security (EMS) products can help you as we head towards May 25, 2018 when the GDPR comes in to effect. At Microsoft, we have both committed to being GDPR compliant as well as providing guidance to you on how you can use our technologies on your GDPR journey. For example, in the whitepaper “ Beginning your GDPR Journey ” we outlined four key steps that can help you start today – Discover (understand what data you have that is in the scope for the GDPR), Manage (Govern how personal data is used and accessed), Protect (Establish security controls to prevent, detect, and respond to vulnerabilities and data breaches), and Report (Keep required documentation, manage data requests, and provide breach notifications). At the core of this approach is the data, which is where EMS can help you, and where we will dive deeper in this blog post. GDPR covers all classes of your stored data, be it structured, logs or unstructured data. All classes have their own challenges but the structured side is more evident to you given, well, the more structured nature of the problem space. For the sake of today’s blog, we’ll presume you have a better idea on how to address those data stores.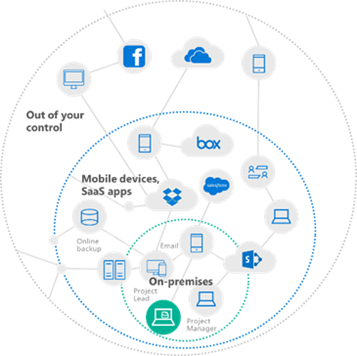 The logs data stores are also somewhat structured but here we find an added complexity: logs related to security often have required retention periods for compliance purposes. If you find yourself in this situation, I would encourage you to review each log type carefully with your internal legal counsel; it’s not sufficient for IT to ‘proclaim’ your log as related to security and thus deem yourself compliant. Given the potential fines associated with GDPR this could be a very costly mistake!
For unstructured data, life had been progressively getting way, way harder. For those who have been following our information protection efforts, you’ll certainly recall this image. In summary, most organizations have shifted from having their data entirely on-premises to now having it often being ‘out of your control’… data is shared with others, sent around in email, given to external vendors (lawyers, marketing, HR, etc). In short, our saying of “For data to be useful, it WILL travel” is most certainly a good cause for concern. It’s worth saying that GDPR is not the only reason to protect personal and sensitive data; we all have this type of data and it should be protected.
What GDPR is doing is putting a date (and price tag) on getting this done as-soon-as-possible. You have practices to protect your data today, but now you need to put additional emphasis for reviewing your current approach and making sure you are following the industry best practices.
To be clear, we at Microsoft have the exact same challenges and we’re in this with you!
OK, so what will it take to get ready? To address this question, first we should start with shedding light on the data lifecycle and explain how we can help you protect your data through several different scenarios throughout this lifecycle. We need to consider what protective measures we should take from when data is created or modified, to when a user wants to access it, when data moves to mobile and cloud apps and even when it gets breached.
In this blog series, you will see how Microsoft EMS solutions can support you in this journey to EU GDPR compliance step-by-step with addressing the following key scenarios:
The logs data stores are also somewhat structured but here we find an added complexity: logs related to security often have required retention periods for compliance purposes. If you find yourself in this situation, I would encourage you to review each log type carefully with your internal legal counsel; it’s not sufficient for IT to ‘proclaim’ your log as related to security and thus deem yourself compliant. Given the potential fines associated with GDPR this could be a very costly mistake!
For unstructured data, life had been progressively getting way, way harder. For those who have been following our information protection efforts, you’ll certainly recall this image. In summary, most organizations have shifted from having their data entirely on-premises to now having it often being ‘out of your control’… data is shared with others, sent around in email, given to external vendors (lawyers, marketing, HR, etc). In short, our saying of “For data to be useful, it WILL travel” is most certainly a good cause for concern. It’s worth saying that GDPR is not the only reason to protect personal and sensitive data; we all have this type of data and it should be protected.
What GDPR is doing is putting a date (and price tag) on getting this done as-soon-as-possible. You have practices to protect your data today, but now you need to put additional emphasis for reviewing your current approach and making sure you are following the industry best practices.
To be clear, we at Microsoft have the exact same challenges and we’re in this with you!
OK, so what will it take to get ready? To address this question, first we should start with shedding light on the data lifecycle and explain how we can help you protect your data through several different scenarios throughout this lifecycle. We need to consider what protective measures we should take from when data is created or modified, to when a user wants to access it, when data moves to mobile and cloud apps and even when it gets breached.
In this blog series, you will see how Microsoft EMS solutions can support you in this journey to EU GDPR compliance step-by-step with addressing the following key scenarios:
 After explaining how EMS technologies can help you with these different use cases, we will share resources to get started with our trial and deployment programs. If you already have EMS and need help with deployment, our FastTrack program can assist!
In the next blog in the series, we’ll start discussing how to protect data persistently on-premises and in the cloud with Azure Information Protection. Before then, we’d recommend that you learn more about these products (if you are not familiar with them) and learn more about the GDPR law (if you have yet to do so).
I encourage you to:
After explaining how EMS technologies can help you with these different use cases, we will share resources to get started with our trial and deployment programs. If you already have EMS and need help with deployment, our FastTrack program can assist!
In the next blog in the series, we’ll start discussing how to protect data persistently on-premises and in the cloud with Azure Information Protection. Before then, we’d recommend that you learn more about these products (if you are not familiar with them) and learn more about the GDPR law (if you have yet to do so).
I encourage you to:
Hi everyone, By now most of you will, at the very least, have heard of the GDPR, the EU’s new law for data protection. GDPR stands for General Data Protection Regulation . Simply put, it aims to protect personal data from potential abuse. As Microsoft’s Chief Privacy Officer, Brendon Lynch mentioned in his blog “ The new General Data Protection Regulation (GDPR) is the most significant change to European Union (EU) privacy law in two decades ”. Today, I’m kicking off a blog series which will frame how we think Microsoft Enterprise Mobility + Security (EMS) products can help you as we head towards May 25, 2018 when the GDPR comes in to effect. At Microsoft, we have both committed to being GDPR compliant as well as providing guidance to you on how you can use our technologies on your GDPR journey. For example, in the whitepaper “ Beginning your GDPR Journey ” we outlined four key steps that can help you start today – Discover (understand what data you have that is in the scope for the GDPR), Manage (Govern how personal data is used and accessed), Protect (Establish security controls to prevent, detect, and respond to vulnerabilities and data breaches), and Report (Keep required documentation, manage data requests, and provide breach notifications). At the core of this approach is the data, which is where EMS can help you, and where we will dive deeper in this blog post. GDPR covers all classes of your stored data, be it structured, logs or unstructured data. All classes have their own challenges but the structured side is more evident to you given, well, the more structured nature of the problem space. For the sake of today’s blog, we’ll presume you have a better idea on how to address those data stores.
 The logs data stores are also somewhat structured but here we find an added complexity: logs related to security often have required retention periods for compliance purposes. If you find yourself in this situation, I would encourage you to review each log type carefully with your internal legal counsel; it’s not sufficient for IT to ‘proclaim’ your log as related to security and thus deem yourself compliant. Given the potential fines associated with GDPR this could be a very costly mistake!
For unstructured data, life had been progressively getting way, way harder. For those who have been following our information protection efforts, you’ll certainly recall this image. In summary, most organizations have shifted from having their data entirely on-premises to now having it often being ‘out of your control’… data is shared with others, sent around in email, given to external vendors (lawyers, marketing, HR, etc). In short, our saying of “For data to be useful, it WILL travel” is most certainly a good cause for concern. It’s worth saying that GDPR is not the only reason to protect personal and sensitive data; we all have this type of data and it should be protected.
What GDPR is doing is putting a date (and price tag) on getting this done as-soon-as-possible. You have practices to protect your data today, but now you need to put additional emphasis for reviewing your current approach and making sure you are following the industry best practices.
To be clear, we at Microsoft have the exact same challenges and we’re in this with you!
OK, so what will it take to get ready? To address this question, first we should start with shedding light on the data lifecycle and explain how we can help you protect your data through several different scenarios throughout this lifecycle. We need to consider what protective measures we should take from when data is created or modified, to when a user wants to access it, when data moves to mobile and cloud apps and even when it gets breached.
In this blog series, you will see how Microsoft EMS solutions can support you in this journey to EU GDPR compliance step-by-step with addressing the following key scenarios:
The logs data stores are also somewhat structured but here we find an added complexity: logs related to security often have required retention periods for compliance purposes. If you find yourself in this situation, I would encourage you to review each log type carefully with your internal legal counsel; it’s not sufficient for IT to ‘proclaim’ your log as related to security and thus deem yourself compliant. Given the potential fines associated with GDPR this could be a very costly mistake!
For unstructured data, life had been progressively getting way, way harder. For those who have been following our information protection efforts, you’ll certainly recall this image. In summary, most organizations have shifted from having their data entirely on-premises to now having it often being ‘out of your control’… data is shared with others, sent around in email, given to external vendors (lawyers, marketing, HR, etc). In short, our saying of “For data to be useful, it WILL travel” is most certainly a good cause for concern. It’s worth saying that GDPR is not the only reason to protect personal and sensitive data; we all have this type of data and it should be protected.
What GDPR is doing is putting a date (and price tag) on getting this done as-soon-as-possible. You have practices to protect your data today, but now you need to put additional emphasis for reviewing your current approach and making sure you are following the industry best practices.
To be clear, we at Microsoft have the exact same challenges and we’re in this with you!
OK, so what will it take to get ready? To address this question, first we should start with shedding light on the data lifecycle and explain how we can help you protect your data through several different scenarios throughout this lifecycle. We need to consider what protective measures we should take from when data is created or modified, to when a user wants to access it, when data moves to mobile and cloud apps and even when it gets breached.
In this blog series, you will see how Microsoft EMS solutions can support you in this journey to EU GDPR compliance step-by-step with addressing the following key scenarios:
- How to provide persistent data protection on-premises and in the cloud
- How to grant and restrict access to data
- How to protect data in mobile devices and applications
- How to gain visibility and control of data in cloud apps
- How to detect data breaches before they cause damage
 After explaining how EMS technologies can help you with these different use cases, we will share resources to get started with our trial and deployment programs. If you already have EMS and need help with deployment, our FastTrack program can assist!
In the next blog in the series, we’ll start discussing how to protect data persistently on-premises and in the cloud with Azure Information Protection. Before then, we’d recommend that you learn more about these products (if you are not familiar with them) and learn more about the GDPR law (if you have yet to do so).
I encourage you to:
After explaining how EMS technologies can help you with these different use cases, we will share resources to get started with our trial and deployment programs. If you already have EMS and need help with deployment, our FastTrack program can assist!
In the next blog in the series, we’ll start discussing how to protect data persistently on-premises and in the cloud with Azure Information Protection. Before then, we’d recommend that you learn more about these products (if you are not familiar with them) and learn more about the GDPR law (if you have yet to do so).
I encourage you to:
- Download our whitepaper explaining how Microsoft EMS supports your GDPR compliance journey
- Watch Microsoft’s webcast to learn more about GDPR and Microsoft’s commitment
- Check out the rest of our content at the Microsoft GDPR website
0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.