- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Successful Security Posture Management: control your SaaS apps via Microsoft Cloud App Security
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Authored with Idan Basre, Product Manager, Microsoft Cloud App Security and Ran Marom, Senior Manager, Product Management, Microsoft Cloud App Security
Security posture is an organization’s built-in resilience to protect against threats and weaknesses like misconfigurations, user authentication misuse, loss of sensitive data, misuse of sessions in real-time, and threats across multi-cloud environments. A security posture management system should continuously report on and improve your organization’s security posture by focusing on disrupting any potential attackers from gaining a return on their investment. Specifically, security posture management in cloud applications should encompass two things-- cloud security posture management (CSPM) and SaaS security posture management (SSPM).
Cloud Security Posture Management
Cloud security posture management should expansively cover your cloud platforms and ensure that configurations are aligned with CIS benchmarks and any misalignments are surfaced for the organization’s consideration. This brief two-minute video demonstrates the abilities of cloud security posture management in Microsoft Cloud App Security:
SaaS Security Posture Management
Let’s drill down into SaaS security. Almost every organization uses cloud applications: Office 365, Box, Salesforce, GitHub, ServiceNow – and more. SaaS applications are becoming essential tools for the daily routine of every business. SaaS applications save your organization time by streamlining app installation and maintenance, reducing cost of licensing, improving the scalability for your end users, and lessening strain of compatibility issues on different platforms.
However, there’s some risk involved. The most sensitive data is stored in those applications–customers’ business and personally identifiable information, patents, employees’ personal details, and even ways to access the organization remotely. SaaS applications should be treated as one of the most precious company assets.
But protecting those apps is not an easy task. Every app has its own administrator and configuration. Even a slight misapplication of policy potentially opens an opportunity for a breach. In order to protect an app, one should know where the sensitive data can be located, or which specific configurations can lead to a breach. It's easy to assume that the app owner had security in mind during creation and deployment. However, an app owner’s goal is typically to enhance the organization’s productivity. Security issues tend to fall to lesser prioritization.
While it might also seem logical that security admins should be able to take care of the security for these apps, the current landscape makes it almost impossible to specialize in every app. An automated approach is needed. Security posture management should surface detection of misconfigurations and continuous assessment of an organization’s security enforcement.
SaaS Security Posture Management (SSPM) aims to solve this problem. As Gartner noted in the Hype Cycle for Cloud Security, 2020, SSPM tools “continuously assess the security risk and manage the security posture of SaaS applications. Core capabilities include reporting the configuration of native SaaS security settings and offering suggestions for improved configuration to reduce risk. Optional capabilities include comparison against industry frameworks and automatic adjustment and reconfiguration.” Organizations use SSPM tools help security admins detect risky misconfigurations and automatically or manually remediate them.
OAuth Application Permission Recommendations
One way that Microsoft Cloud App Security detects risky misconfigurations is with OAuth applications that are connected to your SaaS apps. Cloud App Security gives assessment of those OAuth apps, and has the ability to automatically or manually revoke a connected OAuth app. If a user connects a malicious OAuth app, Cloud App Security detects it and can automatically revoke access to the suspicious app.
Automatic remediation is a key capability that is integral to Microsoft Cloud App Security. Admins can configure it easily via built-in policies or creating customized policies. If automatically revoking the access is too aggressive and harmful to productivity, Microsoft Cloud App Security has the ability to alert only and give the security admin the power to manually revoke access as needed. Here, we see the OAuth management tab for Google, where an admin is digging into the QR code generator for more insights on the usage:
Privileged User Configuration Recommendations
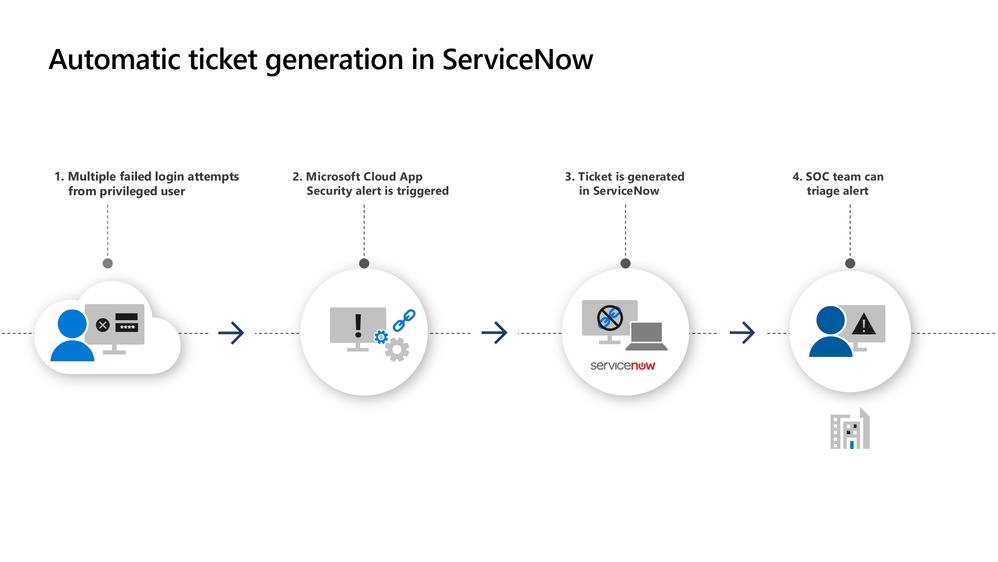
Another critical SSPM capability is recognizing privileged users for each of the SaaS apps deployed in an organization. Privileged users potentially have abilities to change configurations or accidentally share sensitive data to inappropriate levels of exposure. For example, a Salesforce user has the privilege to set a password without an expiration date for other users, or a user is permissioned to schedule data reports and export them. These privileged users, with full or partial permissions, should be carefully and regularly examined. With Microsoft Cloud App Security, admins can detect which users have higher permissions, when these permissions were set, and by whom. If an admin has deployed a connection to Power Automate and ServiceNow, the flow might look something like this:
Information Protection
Information protection is always an important pillar, but even more so in SaaS apps as business-critical data sits outside the corporate network. First, organizations need to control their sensitive data across their SaaS applications by discovering and classifying it, for instance, detecting the presence of sensitive company information in a file and labeling the file as “Highly Confidential”. Second, they need to control end users using this data by limiting who has access to what. And third, prevent users from oversharing by preventing upload or download of sensitive information based on classification.
For additional read about MCAS information protection, here is a dedicated blog by Idan on this subject:
What to do Next
It’s clear that security posture management is essential, and every organization needs both cloud security posture management and SaaS security posture management capabilities. Inappropriate security posture and misconfigurations put an organization at risk, and an automatic approach for application security remediation is highly efficient and effective. Microsoft Cloud App Security gives these capabilities to your security and secops teams, bringing peace of mind to everyone.
For further training or information, view Ran’s twenty-minute discussion on security posture management in Microsoft Cloud App Security:
Feedback
We welcome your feedback or relevant use cases and requirements for this pillar of Cloud App Security by emailing CASFeedback@microsoft.com and mention Security Posture Management.
Learn more
For further information on how your organization can benefit from Microsoft Cloud App Security, connect with us at the links below:
|
Join the conversation on Tech Community. Stay up to date—subscribe to our blog. |
Upload a log file from your network firewall or enable logging via Microsoft Defender for Endpoint to discover Shadow IT in your network. |
|
Learn more—download Top 20 use cases for CASB. |
Connect your cloud apps to detect suspicious user activity and exposed sensitive data. |
|
Search documentation on Microsoft Cloud App Security. |
Enable out-of-the-box anomaly detection policies and start detecting cloud threats in your environment. |
|
Understand your licensing options . |
Continue with more advanced use cases across information protection, compliance, and more. |
|
Follow the Microsoft Cloud App Security Ninja blog and learn about Ninja Training. Go deeper with these interactive guides:
|
|
To experience the benefits of full-featured CASB, sign up for a free trial—Microsoft Cloud App Security.
Follow us on LinkedIn as #CloudAppSecurity. To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity on Twitter, and Microsoft Security on LinkedIn for the latest news and updates on cybersecurity.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.