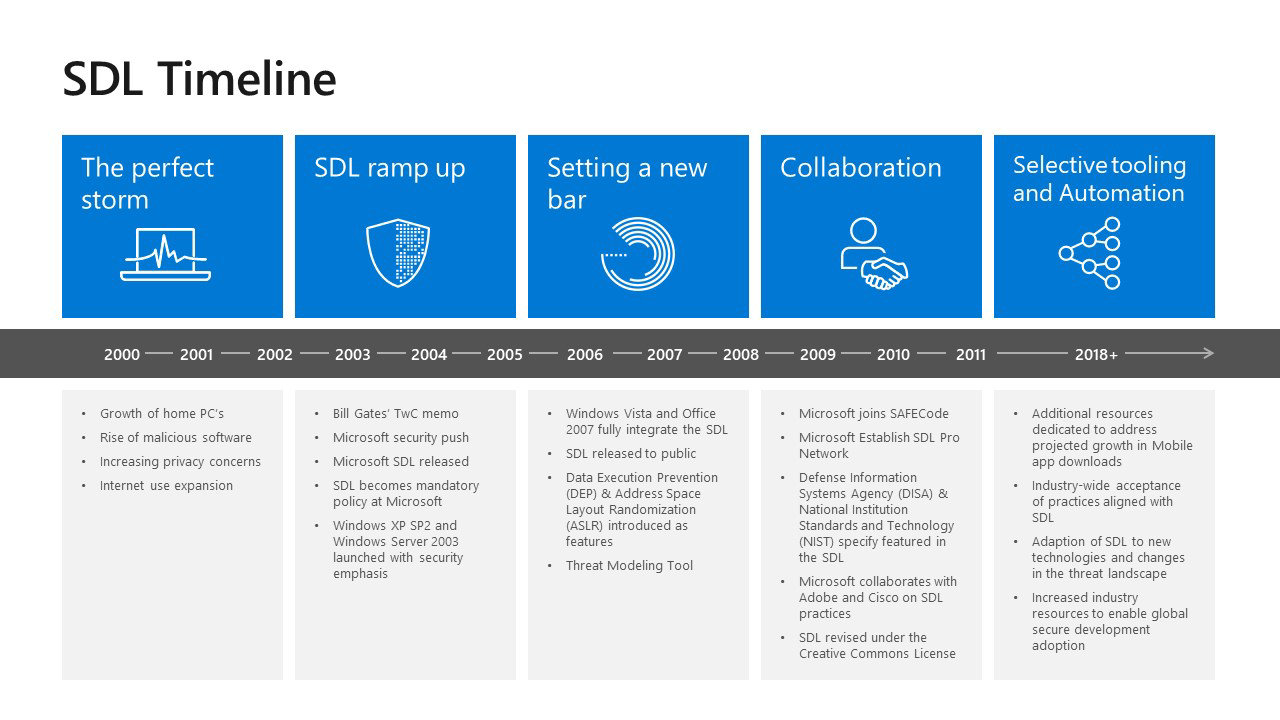
In the early 2000s, personal computers (PCs) were becoming increasingly common in the home and the internet was gaining more widespread use. This led to a rise in malicious software looking to take advantage of users connecting their home PCs to the internet. It quickly became evident that protecting users from malicious software was going to take a fundamentally different approach to security.
In January 2002, Microsoft launched its Trustworthy Computing initiative to help ensure Microsoft products and services were built inherently highly secure, available, reliable, and with business integrity. The Microsoft Security Development Lifecycle (SDL) was an outcome of our software development groups working to develop a security model that’s easy for developers to understand and build into their security code.
The Microsoft SDL became an integral part of the software development process at Microsoft in 2004. The development, implementation, and constant improvement of the SDL represents our strategic investment to the security effort. This is an evolution in the way that software is designed, developed, and tested, and has now matured into a well-defined methodology.
Now, over a decade later, the Microsoft SDL continues to be fundamental to how we develop our products and services. With the rise of mobile, cloud computing, Internet of Things, artificial intelligence, and other new technologies, we’ve continued to evolve the practices.